Check Point Software Bundle
How Did Check Point Software Become a Cybersecurity Giant?
From its humble beginnings in 1993, Check Point Software Technologies has become a cornerstone of the cybersecurity landscape. This Check Point Software SWOT Analysis will help you understand the company's strategic positioning. But how did this Israeli tech startup transform into a global leader, protecting businesses and individuals from ever-evolving cyber threats?

This exploration into the brief history of Check Point Software will reveal the pivotal moments that shaped its trajectory. We'll examine the early days, the innovative spirit of its founders, and the strategic decisions that propelled it to the forefront of the software security industry. Discover the key milestones that transformed Check Point from a firewall pioneer into a comprehensive cybersecurity company.
What is the Check Point Software Founding Story?
The story of Check Point Software Technologies began in 1993 in Ramat Gan, Israel. It was a time when the internet was rapidly expanding, and the need for robust network security was becoming increasingly apparent. This need became the driving force behind the company's creation, setting the stage for its future as a leading cybersecurity company.
The company was co-founded by Gil Shwed, Marius Nacht, and Shlomo Kramer. Gil Shwed, with his background in the elite Unit 8200 of the Israel Defense Forces, developed the core technology that would define Check Point: stateful inspection. This innovation was a game-changer in network security, and it formed the basis of their first product, FireWall-1.
The founders understood that businesses needed a strong security solution to confidently embrace the internet for commercial purposes. Their initial business model focused on providing this protection, recognizing that without it, the adoption of the internet would be slow. Early funding, including a $250,000 investment from BRM Group, helped launch the company. The initial capital amounted to $400,000. Gil Shwed's belief that the internet, while offering access, also presented dangers, was a key philosophy that shaped Check Point's approach to cybersecurity.
Check Point's early days were marked by innovation and a clear vision to secure the growing internet.
- The company's founders identified a critical need for network security solutions.
- Gil Shwed's expertise in military intelligence was instrumental in developing the core technology.
- The initial funding and capital laid the groundwork for Check Point's growth.
- Check Point's early products, like FireWall-1 and VPN-1, set the standard for network security.
Check Point's early focus on network security was prescient. As the internet evolved, so did the threats. The company's early products, such as FireWall-1, which was released in 1994, and VPN-1, were pivotal in shaping the cybersecurity landscape. These products provided essential protection for businesses, allowing them to securely use the internet for commercial activities. The founders' foresight in recognizing the importance of security positioned Check Point at the forefront of the emerging cybersecurity industry. For a deeper understanding of their growth trajectory, consider exploring the Growth Strategy of Check Point Software.
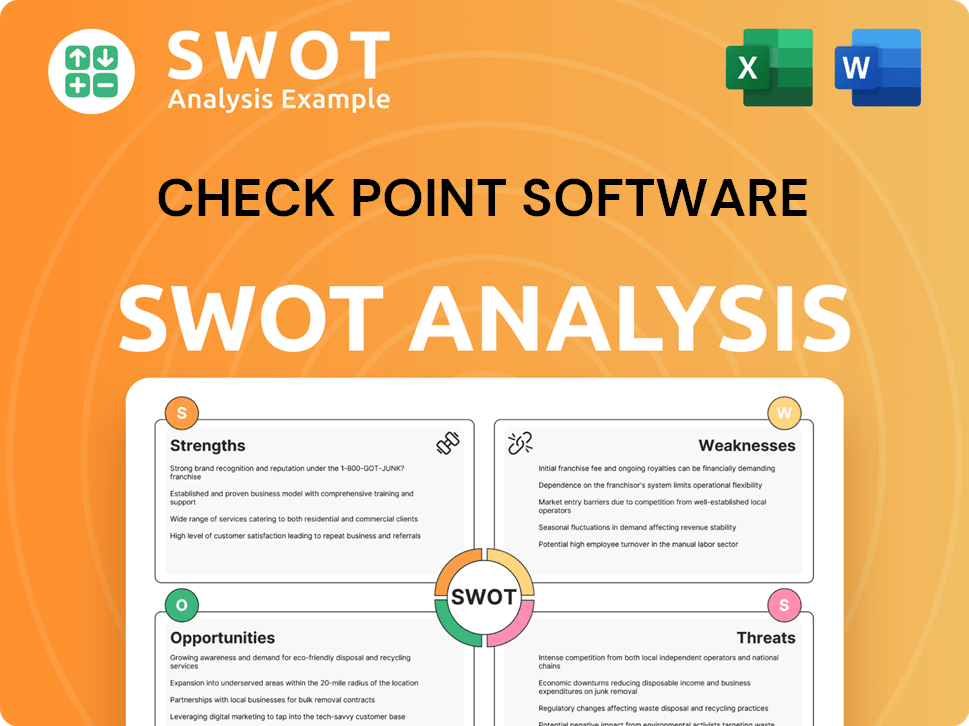
Check Point Software SWOT Analysis
- Complete SWOT Breakdown
- Fully Customizable
- Editable in Excel & Word
- Professional Formatting
- Investor-Ready Format
What Drove the Early Growth of Check Point Software?
The early growth of Check Point Software, a prominent cybersecurity company, was marked by rapid product development and strategic partnerships. Following the release of FireWall-1 in 1994, the company quickly expanded its reach and market presence. This period saw significant milestones, including key partnerships and a successful initial public offering (IPO) that fueled further expansion and innovation.
In its early days, Check Point Software strategically partnered with major players to solidify its market position. In 1994, an OEM agreement was signed with Sun Microsystems, followed by a distribution agreement with HP in 1995. By February 1996, Check Point was recognized as the worldwide firewall market leader by IDC, capturing a substantial 40% market share.
A crucial step in Check Point's growth was its IPO on NASDAQ in June 1996, which raised $67 million. This capital injection facilitated further expansion and innovation. The company established its U.S. head office in Redwood City, California, in the same year, marking a significant geographical expansion.
Check Point Software formed a strategic partnership with Nokia in 1998, bundling its software with Nokia's network security appliances. The company also began acquiring other IT security firms in the early 21st century, including Nokia's network security business unit in 2009. This strategy helped expand its product offerings and market reach.
Check Point expanded its geographical footprint, opening a branch in Delhi, India, in August 2003. For the full fiscal year 2024, the company reported total revenues of $2.565 billion, a 6% increase year-over-year. Security Subscriptions Revenues increased by 13% to $1.104 billion in 2024. As of March 31, 2025, Check Point's trailing 12-month revenue was $2.604 billion, a 6.4% increase year-over-year.
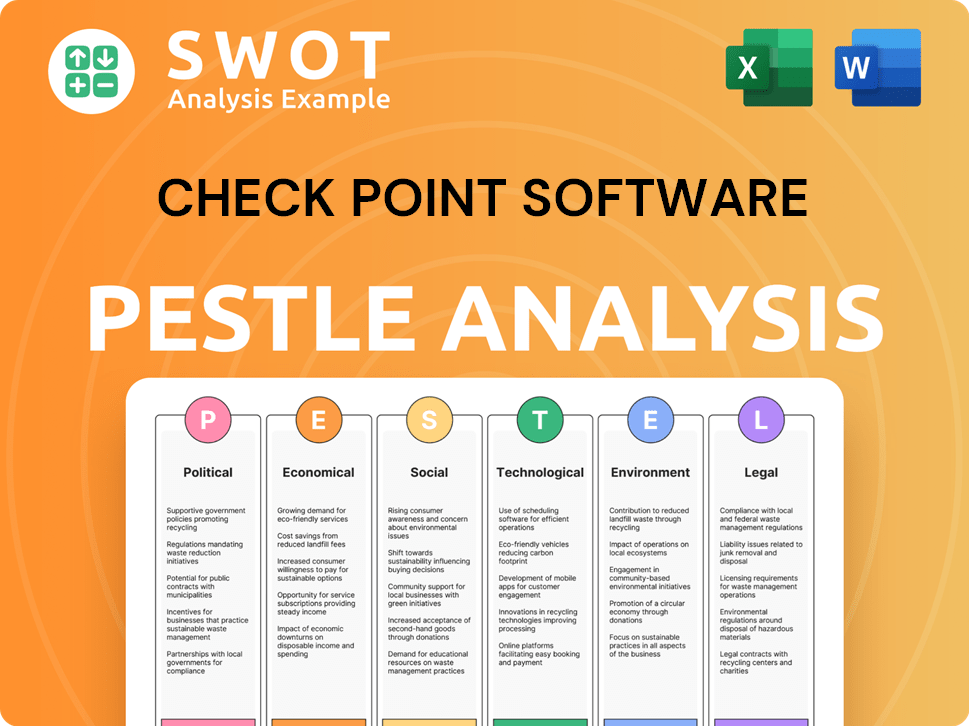
Check Point Software PESTLE Analysis
- Covers All 6 PESTLE Categories
- No Research Needed – Save Hours of Work
- Built by Experts, Trusted by Consultants
- Instant Download, Ready to Use
- 100% Editable, Fully Customizable
What are the key Milestones in Check Point Software history?
The Check Point Software story is marked by significant advancements and strategic shifts in the cybersecurity landscape. From its early days to its current position as a leading cybersecurity company, the company has consistently adapted to the evolving threats and market dynamics.
| Year | Milestone |
|---|---|
| 1993 | Gil Shwed develops stateful inspection technology, a foundational innovation for the company. |
| 1994 | FireWall-1, based on stateful inspection, is released, marking the company's entry into the market. |
| 2006 | The company introduces a unified security architecture with a single management console and unified security gateways. |
| 2009 | Software blade architecture is launched, providing modular and flexible security solutions. |
| 2017 | Check Point Infinity, a consolidated threat prevention platform, is introduced. |
| 2024 | Cyberint acquisition to enhance external risk management. |
| 2024 | Nadav Zafrir appointed as CEO in December. |
| 2025 | Plans to establish an R&D Centre in Bengaluru, India. |
The company's innovations have been pivotal in shaping cybersecurity. The development of stateful inspection technology and the introduction of FireWall-1 were groundbreaking, and the company has consistently evolved its offerings to meet the changing needs of the market.
FireWall-1, released in 1994, was a pioneering product that utilized stateful inspection technology. This marked a significant advancement in network security, establishing the company as a key player in the cybersecurity sector.
VPN-1 was one of the first VPN products in the world, enhancing secure remote access capabilities. This innovation expanded the company's product portfolio and addressed the growing need for secure remote connectivity.
The introduction of a unified security architecture with a single management console streamlined security operations. This architecture improved efficiency and simplified the management of complex security environments.
The software blade architecture provided modular and flexible security solutions, allowing for customization. This allowed customers to tailor their security deployments to their specific needs.
Check Point Infinity, a consolidated threat prevention platform, has become a key strategic focus. This platform offers comprehensive protection across networks, cloud, endpoints, and mobile devices.
The acquisitions of companies like Zone Labs, Hyperwise, Dome9, Avanan, Perimeter 81, and Cyberint have broadened the company's product portfolio. These acquisitions have strengthened the company's capabilities in critical areas like cloud security and SASE.
Despite its successes, the company has faced challenges in the competitive cybersecurity market. These include slower growth rates compared to some competitors and the need to adapt to rapidly changing technologies.
The company has faced challenges in maintaining its market share in the face of aggressive competition. Competitors have sometimes shown higher growth rates, putting pressure on the company's position.
Compared to some peers, the company has been noted for being more conservative in its investment in research and development. This has potentially impacted its ability to innovate and maintain a competitive edge.
The company is focusing on its Infinity platform and expanding its R&D footprint. These efforts aim to reinvigorate growth and maintain competitiveness in a dynamic industry where AI-driven attacks are a prominent concern.
The appointment of Nadav Zafrir as CEO in December 2024 marks a significant strategic shift. Zafrir's priorities include refining go-to-market strategies and driving sustainable growth.
The plan to establish its first Asia-Pacific R&D Centre in Bengaluru, India, in 2025, is a strategic move. This expansion aims to drive innovation in AI-driven threat prevention and SASE.
The cybersecurity market is characterized by rapidly changing technologies and an evolving competitive landscape. The company must continuously adapt to stay ahead of emerging threats and rival companies.
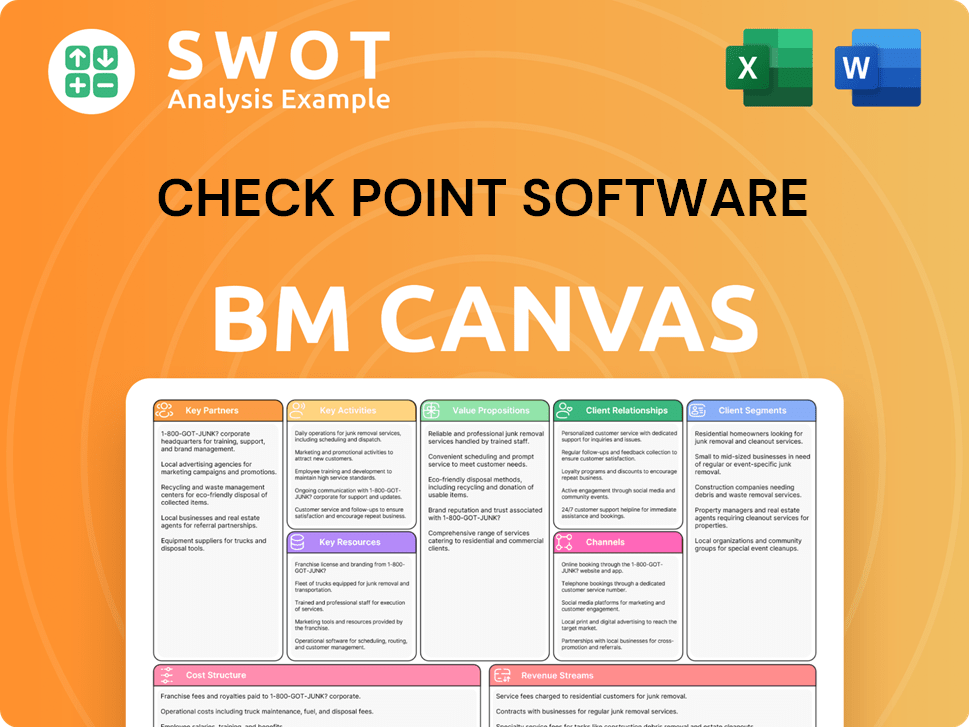
Check Point Software Business Model Canvas
- Complete 9-Block Business Model Canvas
- Effortlessly Communicate Your Business Strategy
- Investor-Ready BMC Format
- 100% Editable and Customizable
- Clear and Structured Layout
What is the Timeline of Key Events for Check Point Software?
The history of Check Point Software Technologies, a prominent cybersecurity company, is marked by significant milestones, from its inception in Israel to its global expansion and technological advancements. Founded in 1993, the company quickly established itself as a leader in the software security industry, pioneering stateful inspection technology with the release of FireWall-1 in 1994. Through strategic acquisitions and continuous innovation, Check Point has evolved to offer comprehensive security solutions, adapting to the ever-changing cyber threat landscape and maintaining its position in the competitive market. Learn more about the Marketing Strategy of Check Point Software.
| Year | Key Event |
|---|---|
| 1993 | Check Point Software Technologies founded in Ramat Gan, Israel, by Gil Shwed, Marius Nacht, and Shlomo Kramer. |
| 1994 | Release of FireWall-1, based on the pioneering stateful inspection technology. |
| 1996 | Initial Public Offering (IPO) on NASDAQ, raising $67 million. |
| 1998 | Partnership with Nokia to bundle Check Point's software with Nokia's security appliances. |
| 2003 | Opening of a branch in Delhi, India. |
| 2004 | Acquisition of Zone Labs for endpoint security. |
| 2009 | Acquisition of Nokia's network security business unit and introduction of Software Blade Architecture. |
| 2017 | Introduction of Check Point Infinity, a consolidated threat prevention security platform. |
| 2018 | Acquisition of Dome9 for cloud security posture management. |
| 2021 | Acquisition of Avanan for cloud email security. |
| 2023 | Acquisition of Perimeter 81 for SASE/SSE platform. |
| 2024 | Acquisition of Cyberint for external risk management platform; Gil Shwed transitions to Executive Chairman, and Nadav Zafrir appointed as new CEO in December. |
| Q4 2024 | Reported $704 million in total revenues, a 6% increase year-over-year, and $959 million in calculated billings, an 11% increase year-over-year. |
| FY 2024 | Reported total revenues of $2.565 billion, a 6% increase year-over-year, and calculated billings of $2.658 billion, a 9% increase year-over-year. |
| Q1 2025 | Reported total operating revenue of $637.8 million, up 6.53% from Q1 2024. |
| 2025 | Plans to establish its first Asia-Pacific Research and Development (R&D) Centre in Bengaluru, India. |
Check Point is heavily investing in AI-driven threat prevention, recognizing the increasing sophistication of cyber threats. The company's 2025 Cyber Security Report predicts a significant increase in AI-driven attacks, emphasizing the need for advanced AI-powered defenses. This focus is crucial for maintaining a competitive edge in the cybersecurity market.
The establishment of an Asia-Pacific R&D Centre in Bengaluru, India, is a key part of Check Point's expansion strategy. This move is designed to enhance the company's ability to develop next-generation cyber defense and AI-driven security management solutions. This expansion is expected to support its global growth trajectory.
In Q1 2025, Check Point reported total operating revenue of $637.8 million, reflecting a 6.53% increase from Q1 2024. For fiscal year 2025, analysts project revenue growth in the range of 5.5% to 6.7% year-over-year, with EPS projections around $9.90 to $10.20. This steady growth is supported by a strong cash position.
Check Point is strategically focused on its Infinity platform, which integrates Quantum network security, CloudGuard for cloud security, Harmony for endpoint and mobile security, and Horizon for security operations management. This platform approach aligns with the industry trend of customers seeking consolidated security solutions to reduce complexity and improve efficiency.
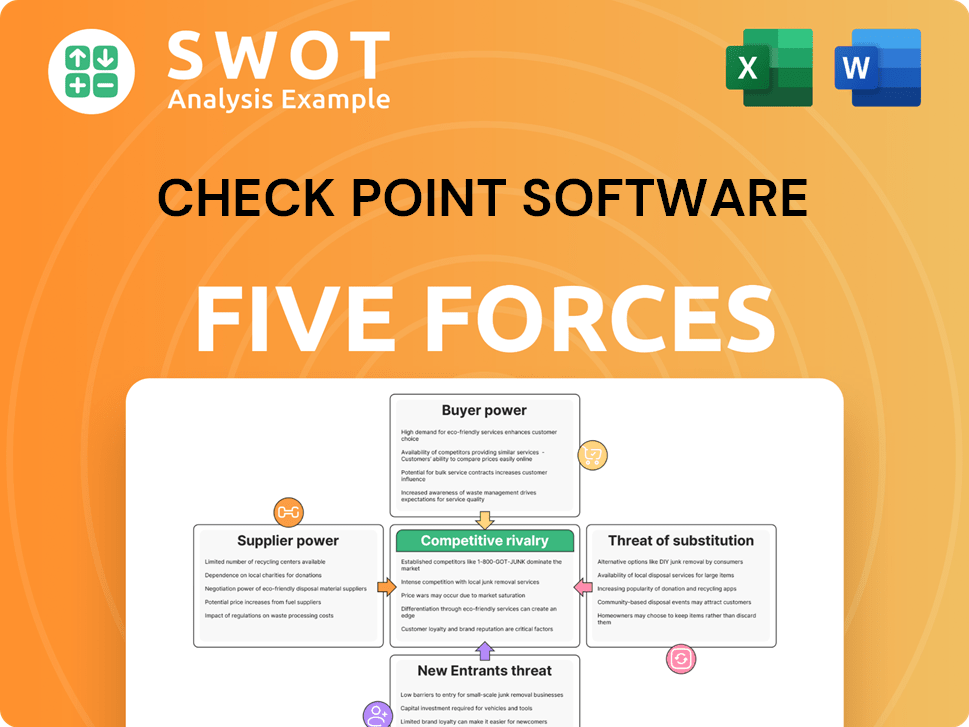
Check Point Software Porter's Five Forces Analysis
- Covers All 5 Competitive Forces in Detail
- Structured for Consultants, Students, and Founders
- 100% Editable in Microsoft Word & Excel
- Instant Digital Download – Use Immediately
- Compatible with Mac & PC – Fully Unlocked
Related Blogs
- What is Competitive Landscape of Check Point Software Company?
- What is Growth Strategy and Future Prospects of Check Point Software Company?
- How Does Check Point Software Company Work?
- What is Sales and Marketing Strategy of Check Point Software Company?
- What is Brief History of Check Point Software Company?
- Who Owns Check Point Software Company?
- What is Customer Demographics and Target Market of Check Point Software Company?
Disclaimer
All information, articles, and product details provided on this website are for general informational and educational purposes only. We do not claim any ownership over, nor do we intend to infringe upon, any trademarks, copyrights, logos, brand names, or other intellectual property mentioned or depicted on this site. Such intellectual property remains the property of its respective owners, and any references here are made solely for identification or informational purposes, without implying any affiliation, endorsement, or partnership.
We make no representations or warranties, express or implied, regarding the accuracy, completeness, or suitability of any content or products presented. Nothing on this website should be construed as legal, tax, investment, financial, medical, or other professional advice. In addition, no part of this site—including articles or product references—constitutes a solicitation, recommendation, endorsement, advertisement, or offer to buy or sell any securities, franchises, or other financial instruments, particularly in jurisdictions where such activity would be unlawful.
All content is of a general nature and may not address the specific circumstances of any individual or entity. It is not a substitute for professional advice or services. Any actions you take based on the information provided here are strictly at your own risk. You accept full responsibility for any decisions or outcomes arising from your use of this website and agree to release us from any liability in connection with your use of, or reliance upon, the content or products found herein.