Check Point Software Bundle
How Does Check Point Software Thrive in the Cybersecurity Arena?
Check Point Software Technologies stands as a global cybersecurity powerhouse, protecting over 100,000 organizations worldwide. With a strong financial performance, including a 6% year-over-year revenue increase in 2024, Check Point demonstrates its resilience and strategic prowess. Its comprehensive suite of solutions, from Check Point Software SWOT Analysis to advanced threat prevention, positions it at the forefront of digital security.

This analysis will explore the inner workings of this leading cybersecurity company, examining its core operations and revenue streams. We'll delve into how Check Point security solutions, including its renowned Check Point firewall, safeguard businesses against evolving threats. Understanding Check Point's approach is essential for anyone navigating the complex world of network security and threat prevention.
What Are the Key Operations Driving Check Point Software’s Success?
Check Point Software Technologies creates value through its comprehensive cybersecurity platform, the Infinity Platform. This platform is designed to protect various digital environments, including networks, endpoints, clouds, and mobile devices. The company's offerings cater to enterprises, service providers, small and medium-sized businesses, and consumers, ensuring broad market coverage.
The core products and services are categorized under Check Point Harmony for workspace security, Check Point CloudGuard for cloud security, Check Point Quantum for network security, and Check Point Infinity Platform Services for collaborative security operations. These solutions are designed to provide robust protection across different attack surfaces.
Operational processes are geared towards continuous technology development, leveraging AI and machine learning to enhance threat prevention. This approach allows for proactive security measures, faster response times, and unified security management, ultimately reducing risk and enhancing digital trust.
Check Point Software emphasizes continuous technology development, using AI and machine learning to improve threat prevention. The company's Quantum Firewall Software R82, launched in late 2024, incorporates new AI engines. This helps block zero-day threats like phishing, malware, and DNS exploits.
In May 2025, Check Point introduced AI-powered Quantum Force Branch Office Security Gateways, enhancing security. These gateways offer up to a 4x increase in threat prevention performance. They also boast a 99.9% block rate, demonstrating the effectiveness of AI in their solutions.
Check Point utilizes a hybrid mesh network architecture with SASE (Secure Access Service Edge) at its core. This architecture unifies management across on-premises, cloud, and workspace environments. It provides flexibility, simplicity, and scale for its customers.
The company supports its supply chain and distribution networks through a wide partner network. This network facilitates supply and deployment, ensuring that customers receive timely and effective security solutions. This approach is key to Check Point's operational efficiency.
Check Point's value proposition is centered on security efficacy, AI-driven solutions, and a comprehensive platform approach. This integrated approach provides proactive threat anticipation and faster response times. Customers benefit from unified security management, which reduces risk and builds digital trust.
- Proactive Threat Anticipation: Utilizing AI to predict and prevent threats before they impact systems.
- Faster Response Times: Rapidly addressing security incidents to minimize damage.
- Unified Security Management: Simplifying security operations across all environments.
- Risk Reduction and Digital Trust: Enhancing overall security posture and building confidence.
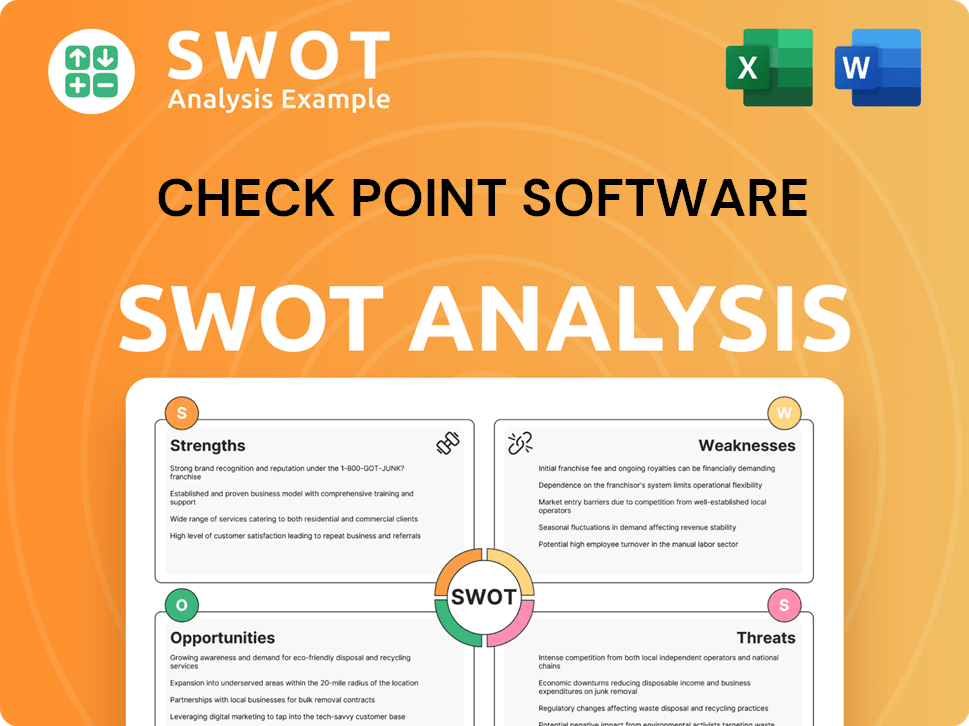
Check Point Software SWOT Analysis
- Complete SWOT Breakdown
- Fully Customizable
- Editable in Excel & Word
- Professional Formatting
- Investor-Ready Format
How Does Check Point Software Make Money?
Check Point Software Technologies, a prominent cybersecurity company, generates revenue mainly through product sales, licenses, and security subscriptions. The company's financial strategy focuses on a balanced approach, leveraging both hardware and software solutions to meet diverse customer needs. This diversified revenue model supports its strong market position and growth prospects.
The company's monetization strategies involve bundling services and tiered pricing, particularly through its Infinity Platform, which integrates various security solutions. This approach allows Check Point to offer comprehensive security packages, enhancing customer value and driving recurring revenue streams. The company's focus on innovation and customer-centric solutions is key to its financial success.
In 2024, Check Point reported total revenues of $2.565 billion. Security Subscriptions were a major contributor, reaching $1.104 billion, a 13% increase year-over-year. The company's performance in Q1 2025 further illustrates its revenue growth. Total revenues for Q1 2025 were $638 million, a 7% increase year-over-year, with Products and Licenses revenues up 14% and Security Subscriptions revenues up 10%.
Check Point's revenue streams are diversified, with a strong emphasis on security subscriptions and product sales. The company's ability to innovate and adapt to evolving cybersecurity threats is crucial for its continued success. The Growth Strategy of Check Point Software showcases its strategic initiatives.
- Security Subscriptions: A significant revenue source, growing by 13% year-over-year in 2024, reaching $1.104 billion.
- Products and Licenses: Products and Licenses revenues saw a notable 14% increase year-over-year in Q1 2025, reaching $114 million.
- Infinity Platform: The AI-driven platform has shown impressive double-digit year-over-year growth in products and licenses revenues.
- Quantum Force Appliance Business: Delivered strong 8% revenue growth in 2024, driven by refresh cycles and new projects.
- Remaining Performance Obligation (RPO): Reached $2.4 billion as of March 31, 2025, an 11% increase year-over-year, indicating strong future revenue visibility.
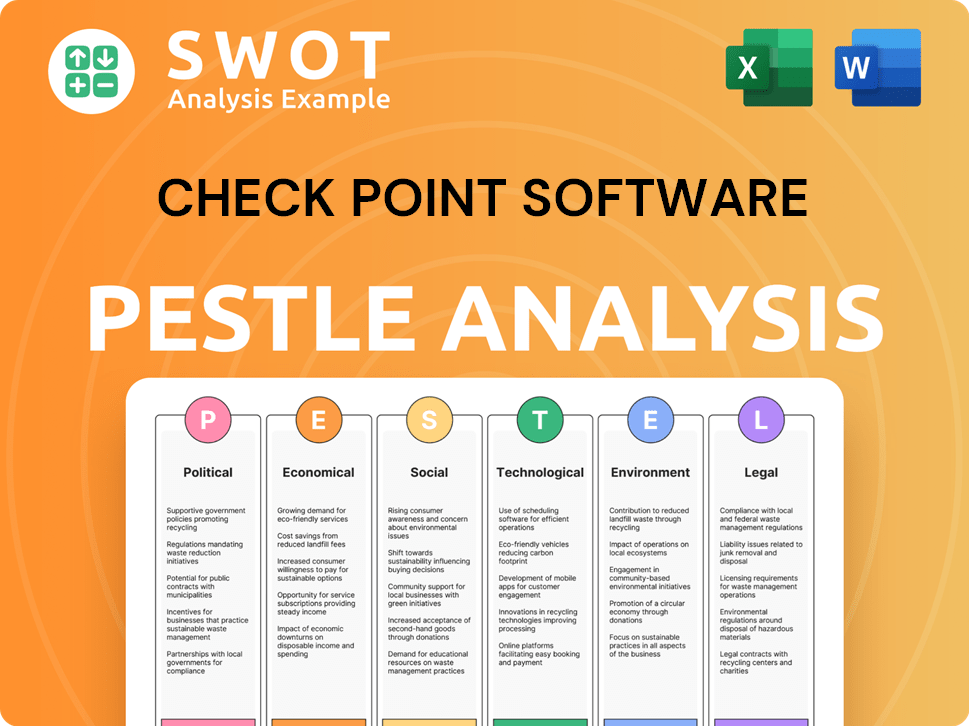
Check Point Software PESTLE Analysis
- Covers All 6 PESTLE Categories
- No Research Needed – Save Hours of Work
- Built by Experts, Trusted by Consultants
- Instant Download, Ready to Use
- 100% Editable, Fully Customizable
Which Strategic Decisions Have Shaped Check Point Software’s Business Model?
The cybersecurity landscape has seen significant developments, and Check Point Software Technologies has been at the forefront, driving innovation and strategic growth. Key milestones and strategic moves have been instrumental in shaping its position in the industry. The company's focus on AI-driven solutions and strategic acquisitions highlights its commitment to staying ahead of evolving cyber threats.
Check Point's strategic initiatives, particularly its AI-powered advancements and acquisitions, are designed to enhance its capabilities and expand its market presence. These moves are crucial for addressing the increasing sophistication of cyber threats. The company's competitive advantages are evident in its technology leadership and prevention-first approach, which are key to its sustained success.
The company's recent activities underscore its dedication to innovation and strategic expansion. From AI-powered security solutions to strategic acquisitions, Check Point is actively shaping its future in the cybersecurity market. This proactive approach is essential for maintaining its competitive edge and addressing the ever-changing threat landscape.
Check Point has consistently enhanced its AI-driven Infinity Platform, a key driver for growth. This has resulted in impressive double-digit year-over-year growth in products and licenses revenues in Q1 2025. The launch of new AI-powered Quantum Force Branch Office Security Gateways in May 2025, offering a 4x increase in threat prevention performance, is another significant milestone.
Strategic acquisitions have been a central part of Check Point's growth strategy. The acquisition of Cyberint Technologies Ltd. in August 2024 enhanced its Security Operations Center (SOC) capabilities. The recent acquisition of Veriti Cybersecurity in May 2025 further strengthens its data security offerings. These moves reflect the company's proactive approach to expanding its capabilities.
Check Point's competitive edge stems from its brand strength, technology leadership, and prevention-first approach. It is recognized as a Leader and Outperformer in GigaOm's 2025 Radar for Enterprise Firewall report. The company's comprehensive Infinity Platform unifies security across various environments, offering flexibility, simplicity, and scale. Check Point continues to adapt to new trends and technology shifts.
Check Point addresses operational and market challenges through continuous innovation, particularly in response to the increasing sophistication of cyber threats. The 2025 Security Report highlighted a 44% increase in global cyber-attacks year-over-year. The company focuses on developing AI-powered tools tailored to unique environments, as stated by Dr. Dorit Dor, emphasizing the role of AI in both attacks and protections.
Check Point's focus on AI and strategic acquisitions is shaping its future. The company is investing in AI-driven solutions to enhance threat detection and response, as seen with the new Quantum Smart-1 Management Appliances launched in May 2025. These appliances integrate AI-powered security tools for faster threat detection and response in hybrid enterprises.
- The acquisition of Cyberint Technologies Ltd. in August 2024 enhanced SOC capabilities.
- The acquisition of Veriti Cybersecurity in May 2025 strengthened data security offerings.
- The company is preparing for quantum computing threats and addressing the misuse of AI in business operations.
- For more insights, explore the growth strategy of Check Point Software.
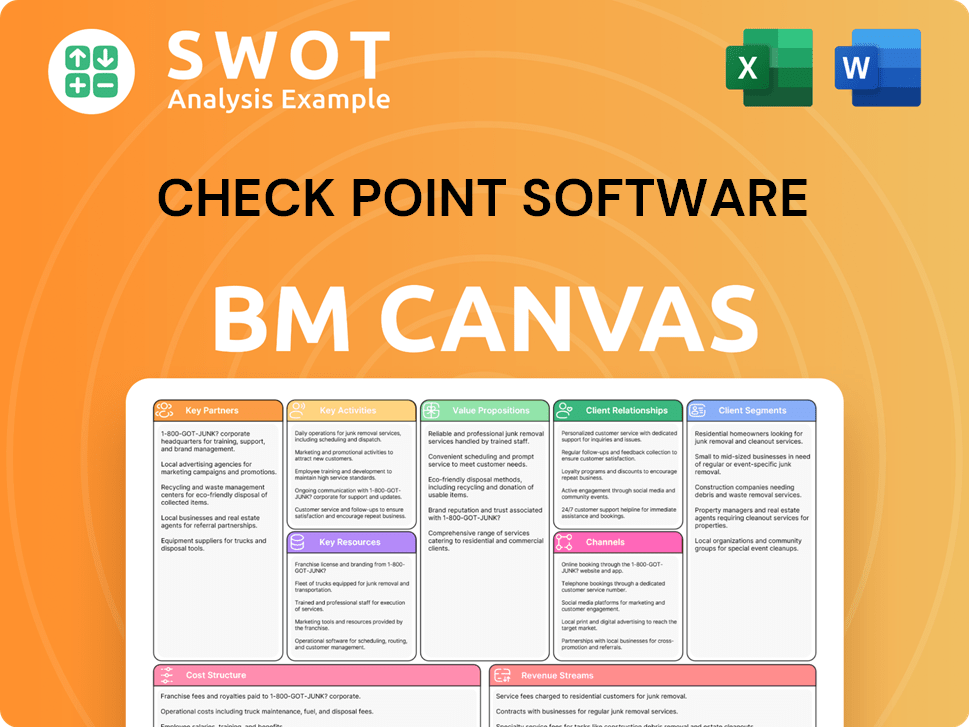
Check Point Software Business Model Canvas
- Complete 9-Block Business Model Canvas
- Effortlessly Communicate Your Business Strategy
- Investor-Ready BMC Format
- 100% Editable and Customizable
- Clear and Structured Layout
How Is Check Point Software Positioning Itself for Continued Success?
In the competitive cybersecurity landscape, Check Point Software maintains a significant presence. The company is recognized as a global leader in cybersecurity solutions, safeguarding over 100,000 organizations worldwide. Check Point security solutions are known for their robust ecosystem and continuous innovation, particularly with its AI-driven Infinity Platform, which contributes to strong customer loyalty.
The company's industry position is further defined by its global revenue distribution, with approximately 50% from EMEA, 40% from the Americas, and 10% from Asia-Pacific. However, the company faces risks such as the rapid evolution of cyber threats and the emergence of new competitors. Strategic initiatives and innovation roadmaps, with a strong focus on AI and platform consolidation, are shaping its future outlook.
As of Q4 2024, Check Point Software Technologies held a market share of 2.58% in the cybersecurity market. This places them in competition with major players like Symantec (33.21%), McAfee (14.80%), and TitanHQ (9.86%). Despite the competition, Check Point is a leader in the cybersecurity market.
Key risks include the rapid evolution of cyber threats, especially AI-driven attacks, which are expected to become more prominent in 2025. Quantum computing poses a threat to encryption methods, requiring organizations to adopt quantum-safe encryption. The cybersecurity market is highly dynamic, with new competitors and technological disruptions constantly emerging.
Check Point's future outlook is shaped by strategic initiatives and innovation, with a strong focus on AI and platform consolidation. The company aims to drive market share expansion and accelerate growth. The acquisition of Veriti Cybersecurity in May 2025 aligns with its 'hybrid mesh security vision,' indicating a focus on proactive security.
The projected revenue growth for 2025 is between 5.5% and 6.7%. This growth rate is a key factor in assessing the company's long-term market position. The company anticipates a significant impact from SASE offerings on revenues starting in 2025.
The company's commitment to a prevention-first approach and investment in AI and comprehensive security solutions positions it to sustain and expand its revenue generation in the evolving cybersecurity landscape. For further insights into Check Point's strategic approach, you can explore the Marketing Strategy of Check Point Software.
Check Point is focusing on AI integration and expansion initiatives. This is designed to enhance user experiences and drive innovation-led revenue growth. The company is also emphasizing platform consolidation to streamline its offerings and improve efficiency.
- AI-driven Infinity Platform
- Hybrid Mesh Security Vision
- SASE offerings starting in 2025
- Proactive Security and Automated Remediation
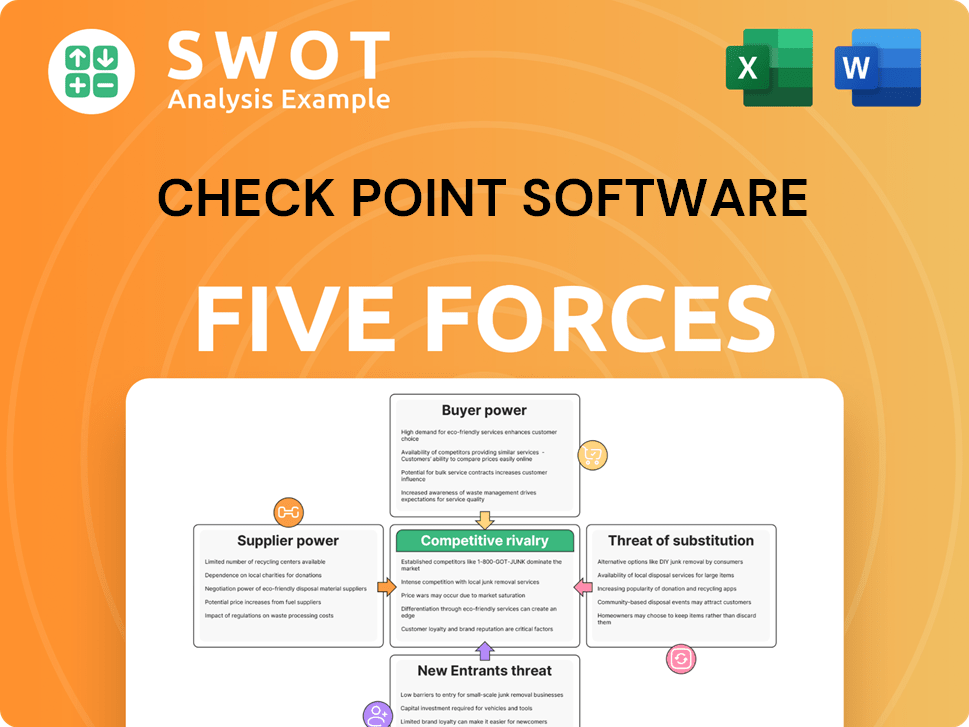
Check Point Software Porter's Five Forces Analysis
- Covers All 5 Competitive Forces in Detail
- Structured for Consultants, Students, and Founders
- 100% Editable in Microsoft Word & Excel
- Instant Digital Download – Use Immediately
- Compatible with Mac & PC – Fully Unlocked
Related Blogs
- What are Mission Vision & Core Values of Check Point Software Company?
- What is Competitive Landscape of Check Point Software Company?
- What is Growth Strategy and Future Prospects of Check Point Software Company?
- What is Sales and Marketing Strategy of Check Point Software Company?
- What is Brief History of Check Point Software Company?
- Who Owns Check Point Software Company?
- What is Customer Demographics and Target Market of Check Point Software Company?
Disclaimer
All information, articles, and product details provided on this website are for general informational and educational purposes only. We do not claim any ownership over, nor do we intend to infringe upon, any trademarks, copyrights, logos, brand names, or other intellectual property mentioned or depicted on this site. Such intellectual property remains the property of its respective owners, and any references here are made solely for identification or informational purposes, without implying any affiliation, endorsement, or partnership.
We make no representations or warranties, express or implied, regarding the accuracy, completeness, or suitability of any content or products presented. Nothing on this website should be construed as legal, tax, investment, financial, medical, or other professional advice. In addition, no part of this site—including articles or product references—constitutes a solicitation, recommendation, endorsement, advertisement, or offer to buy or sell any securities, franchises, or other financial instruments, particularly in jurisdictions where such activity would be unlawful.
All content is of a general nature and may not address the specific circumstances of any individual or entity. It is not a substitute for professional advice or services. Any actions you take based on the information provided here are strictly at your own risk. You accept full responsibility for any decisions or outcomes arising from your use of this website and agree to release us from any liability in connection with your use of, or reliance upon, the content or products found herein.