Check Point Software Bundle
Who Does Check Point Software Protect?
In today's digital age, understanding the Check Point Software SWOT Analysis is crucial for any cybersecurity company aiming for market dominance. The evolution of cyber threats necessitates a deep dive into the customer demographics and target market of industry leaders like Check Point Software. This comprehensive analysis goes beyond simple demographics, exploring the strategic adaptations needed to secure a diverse clientele in an ever-changing digital landscape. Founded in 1993, Check Point initially focused on corporate network security, but its customer base has since expanded significantly.

This shift reflects Check Point Software's agility in responding to evolving market demands and technological advancements. This Market Analysis will explore the customer profile, target audience analysis, and customer segmentation, providing insights into who Check Point's customers are, what their security imperatives entail, and how the company strategically adapts its offerings to serve this expanding market. We will delve into the company's customer acquisition strategy and customer retention strategies, examining the needs and pain points of both small business customers and enterprise customers.
Who Are Check Point Software’s Main Customers?
When examining the Customer Demographics and Target Market of Check Point Software, it's crucial to understand its primary focus on business-to-business (B2B) clients. This Cybersecurity Company primarily serves enterprises, service providers, and small and medium-sized businesses (SMBs). While offering some consumer solutions, the majority of its strategic efforts and revenue are directed toward organizational clients.
Check Point Software's market strategy centers on providing robust security solutions to protect IT infrastructures, sensitive data, and critical applications from cyber threats. The company's customer base spans various industries, including finance, government, healthcare, manufacturing, and technology. This broad reach highlights the universal need for advanced cybersecurity measures across different sectors.
The company's customer segmentation is primarily based on organizational size, industry, and the complexity of their IT environments. Check Point Software continues to derive a significant portion of its revenue from large enterprises, reflecting the substantial investments these organizations make in cybersecurity. However, the SMB market and cloud security offerings are areas of notable growth. The increased demand for cybersecurity solutions among smaller organizations and the shift to cloud-based services are driving this expansion.
Check Point Software caters to large enterprises across various sectors like finance, government, and healthcare. These customers require comprehensive security solutions to protect complex IT infrastructures and sensitive data. The enterprise segment represents a significant portion of Check Point Software's revenue, indicating the importance of these clients in its business strategy.
The service provider segment includes telecommunication companies and managed security service providers (MSSPs). These entities leverage Check Point Software's technologies to offer secure services to their own clients. This segment is crucial for expanding market reach and providing specialized security solutions.
Small and medium-sized businesses (SMBs) represent a growing segment for Check Point Software. The increasing awareness of cyber risks and the need for enterprise-grade security solutions drive this growth. SMBs are looking for easy-to-manage and deploy security solutions.
Cloud security offerings are a key growth area. As businesses increasingly adopt cloud-based services, the demand for cloud-specific security solutions rises. Check Point Software is adapting to this trend by providing robust cloud security products.
The company's focus on B2B clients and the diverse industries it serves highlight its commitment to providing comprehensive cybersecurity solutions. For more insights, you can explore the Revenue Streams & Business Model of Check Point Software.
Check Point Software's customer base is defined by organizational size, industry vertical, and IT environment complexity. The company's customer acquisition strategy involves targeting businesses with complex security needs.
- Large Enterprises: Require advanced, scalable solutions.
- Service Providers: Use Check Point Software's technology to deliver services.
- SMBs: Seeking easy-to-manage security solutions.
- Cloud-Adoption: Driving the demand for cloud security offerings.
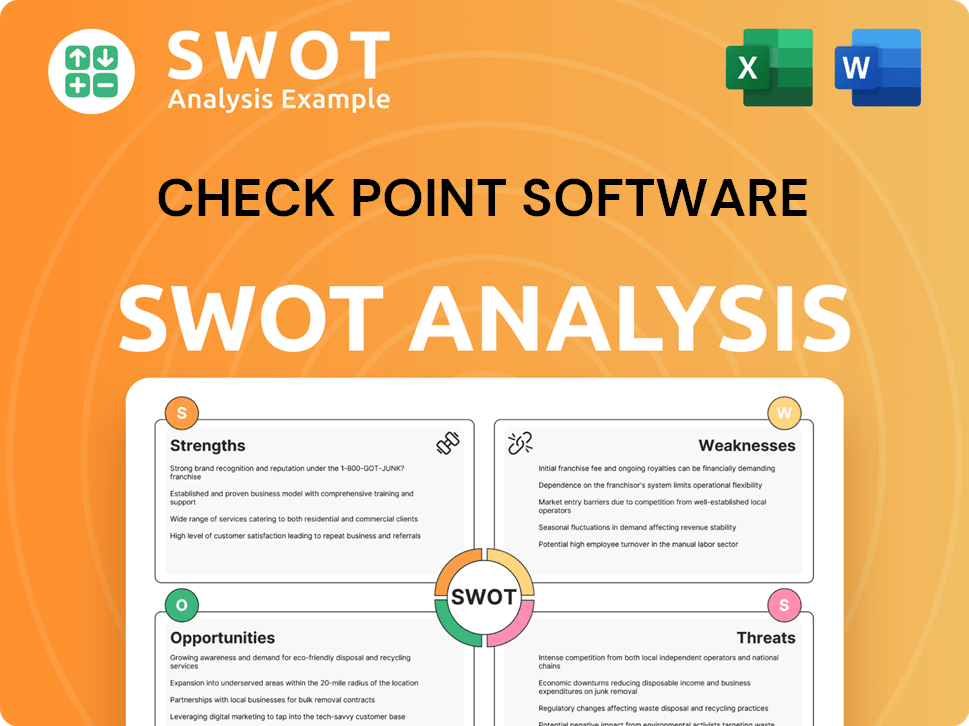
Check Point Software SWOT Analysis
- Complete SWOT Breakdown
- Fully Customizable
- Editable in Excel & Word
- Professional Formatting
- Investor-Ready Format
What Do Check Point Software’s Customers Want?
Understanding the needs and preferences of Check Point Software's customers is crucial for effective market positioning and product development. The primary focus of Check Point Software's customer base revolves around robust and comprehensive cybersecurity solutions. These customers seek to protect their digital assets and ensure business continuity in an increasingly threatening cyber landscape.
The core needs of Check Point Software's customers are driven by the necessity to protect against a wide array of cyber threats. This includes safeguarding against ransomware, phishing, malware, and zero-day exploits across various attack vectors. Additionally, customers prioritize solutions that simplify security management, as IT teams often face resource constraints and the complexity of managing multiple security tools.
Purchasing decisions are significantly influenced by compliance requirements, the escalating costs associated with data breaches, and the imperative to maintain uninterrupted business operations. These factors highlight the importance of understanding the evolving demands of Check Point Software's target market and tailoring solutions to meet their specific needs.
Check Point Software's customers, including both small businesses and large enterprises, consistently prioritize comprehensive and integrated cybersecurity solutions. They are driven by the need to protect against a wide range of threats, manage security efficiently, and comply with industry regulations. Key preferences include ease of deployment, scalability, and integration with existing IT infrastructure.
- Comprehensive Threat Protection: Customers require solutions that protect against a wide array of threats, including ransomware, phishing, malware, and zero-day exploits. According to a 2024 report by Cybersecurity Ventures, global ransomware damage costs are projected to reach $265 billion by 2031.
- Simplified Security Management: IT teams often face resource constraints, making simplified security management a critical need. Check Point Software addresses this by offering consolidated platforms and unified security management.
- Compliance and Business Continuity: Compliance with regulations like GDPR and HIPAA, along with the need to maintain business continuity, are significant drivers. The average cost of a data breach in 2023 was $4.45 million, according to IBM's Cost of a Data Breach Report.
- Real-Time Threat Intelligence and Automation: Customers value solutions that provide real-time threat intelligence and automated responses. This minimizes human intervention and speeds up incident response times.
- Scalability and Integration: The ability to scale security solutions to meet future needs and integrate with existing IT infrastructure is crucial. This ensures that the security measures can adapt as the business grows and evolves.
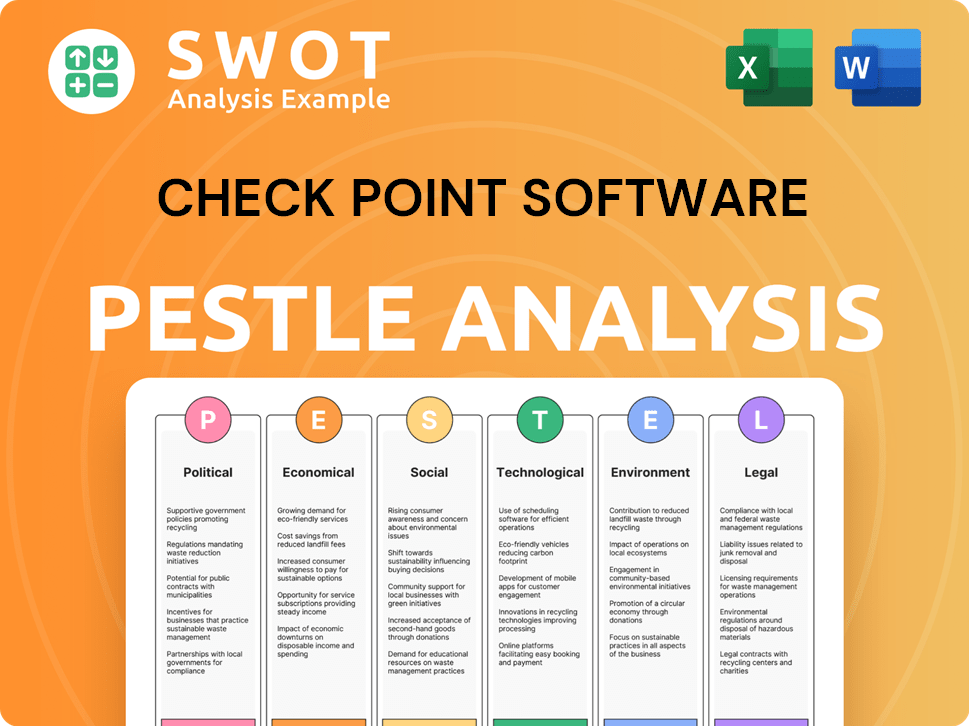
Check Point Software PESTLE Analysis
- Covers All 6 PESTLE Categories
- No Research Needed – Save Hours of Work
- Built by Experts, Trusted by Consultants
- Instant Download, Ready to Use
- 100% Editable, Fully Customizable
Where does Check Point Software operate?
Check Point Software Technologies, a leading cybersecurity company, boasts a robust global presence. Its geographical market spans across North America, Europe, and the Asia-Pacific region, where it has established a strong foothold. The company's strategic approach is tailored to meet the diverse needs of its customer base worldwide, ensuring its solutions are relevant and effective in various markets.
The United States is often a significant revenue generator for Check Point Software, reflecting its strong market share and brand recognition. Western European countries, including the United Kingdom, Germany, and France, are also key markets. In the Asia-Pacific region, Japan, Australia, and India represent important growth areas, with increasing adoption of advanced cybersecurity solutions.
Understanding the nuances of each region is crucial for Check Point Software. Differences in customer demographics, preferences, and buying power influence its strategies. For instance, data privacy regulations vary significantly across regions, necessitating localized compliance features in its offerings. The company adapts its product features to meet regional compliance standards, provides support in local languages, and establishes regional sales and support teams.
Check Point Software localizes its products to meet regional compliance standards. This includes adapting features to comply with specific data privacy regulations, such as GDPR in Europe or CCPA in California. These adjustments ensure that the company's offerings remain relevant and compliant in diverse markets.
The company offers support in multiple languages to cater to its global customer base. This multilingual support includes customer service, technical documentation, and training materials, ensuring that customers can easily understand and utilize Check Point Software's products.
Check Point Software establishes regional sales and support teams to provide tailored services. These teams are familiar with local market dynamics and customer needs, enabling them to offer personalized assistance and build strong customer relationships.
Check Point Software often engages in strategic partnerships with local distributors, resellers, and managed security service providers (MSSPs). These partnerships enhance its reach and provide tailored services within diverse markets, helping to expand its customer base.
Marketing efforts are also localized to resonate with cultural nuances and regional threat landscapes. Check Point Software often partners with local distributors, resellers, and MSSPs to enhance its reach. Recent expansions have focused on emerging markets where digital transformation is accelerating, leading to increased demand for robust cybersecurity solutions. For more insights on the company's structure, consider reading about the Owners & Shareholders of Check Point Software.
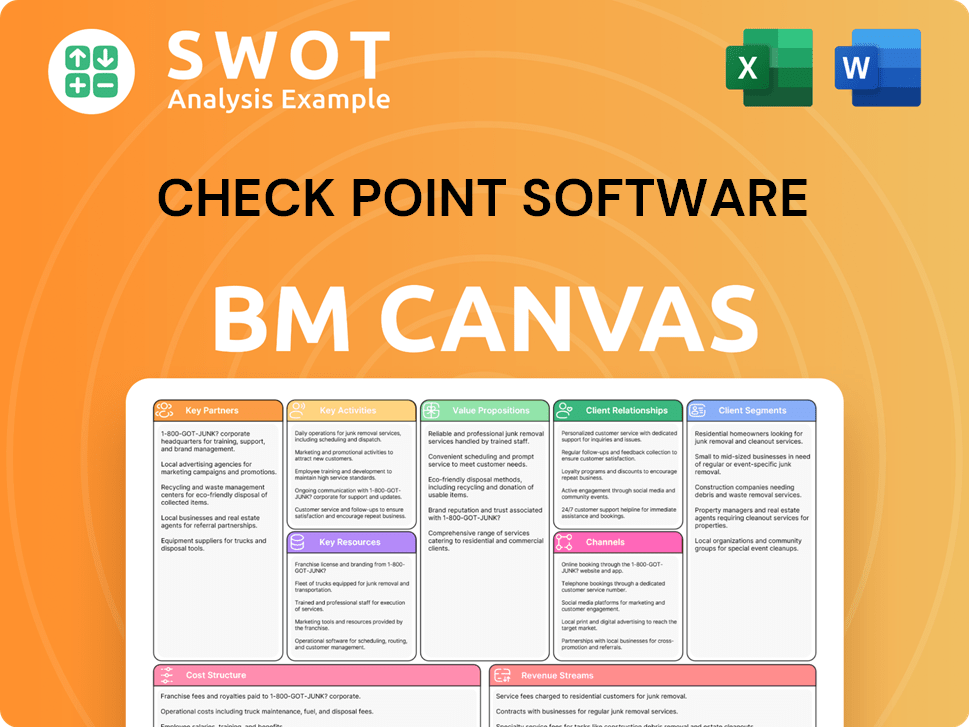
Check Point Software Business Model Canvas
- Complete 9-Block Business Model Canvas
- Effortlessly Communicate Your Business Strategy
- Investor-Ready BMC Format
- 100% Editable and Customizable
- Clear and Structured Layout
How Does Check Point Software Win & Keep Customers?
Check Point Software Technologies, a prominent Cybersecurity Company, employs a multifaceted approach to acquiring and retaining customers. Their strategy combines direct sales, partnerships, and digital marketing to reach a diverse Target Market. The company focuses on delivering value through continuous product innovation, regular updates, and responsive customer support to maintain customer loyalty.
For customer acquisition, Check Point utilizes digital advertising, content marketing, and industry events. They also rely heavily on a global network of channel partners, including value-added resellers and system integrators. Sales tactics often involve a consultative approach, highlighting the value of their integrated security architecture. This approach helps address specific customer needs and compliance requirements.
Customer data and CRM systems play a crucial role in segmenting the market and tailoring campaigns. This enables personalized messaging based on industry, company size, and existing security infrastructure. Successful campaigns emphasize their prevention-first philosophy and unified security management. For retention, they focus on product innovation, updates, and customer support. They also emphasize subscription-based services and cloud-delivered security to foster stronger retention rates.
Check Point Software leverages various channels for customer acquisition. These include digital advertising, content marketing (whitepapers, webinars), and participation in industry conferences. The company also utilizes a robust network of channel partners, which include value-added resellers and system integrators, to extend its market reach. This multi-channel strategy helps in reaching a broad Customer Demographics.
The sales strategy often involves a consultative approach, demonstrating the value of Check Point’s integrated security architecture. Marketing campaigns highlight the company's prevention-first philosophy and unified security management. They tailor campaigns based on Customer Segmentation, considering industry, company size, and existing security infrastructure to deliver personalized messaging.
Check Point focuses on delivering continuous value through product innovation, regular software updates, and responsive customer support. They offer long-term contracts and preferential support tiers. The shift towards subscription-based services and cloud-delivered security enhances retention rates. This approach aims to reduce churn rates and enhance customer loyalty in the competitive cybersecurity market.
Channel partnerships are crucial for Check Point, extending their reach and market penetration. These partnerships include value-added resellers, system integrators, and managed security service providers. By working with partners, Check Point can offer specialized solutions and services to a wider audience, which is a key aspect of their Customer Acquisition Strategy.
Check Point's success in customer acquisition and retention hinges on several key strategies. These include a focus on prevention-first security, a consultative sales approach, and a commitment to continuous product improvement. The company's ability to adapt to the evolving cybersecurity landscape, coupled with a strong partner network, contributes to its sustained growth and customer loyalty.
- Emphasis on integrated security architecture.
- Personalized messaging based on Customer Segmentation.
- Continuous product innovation and updates.
- Strong channel partner network.
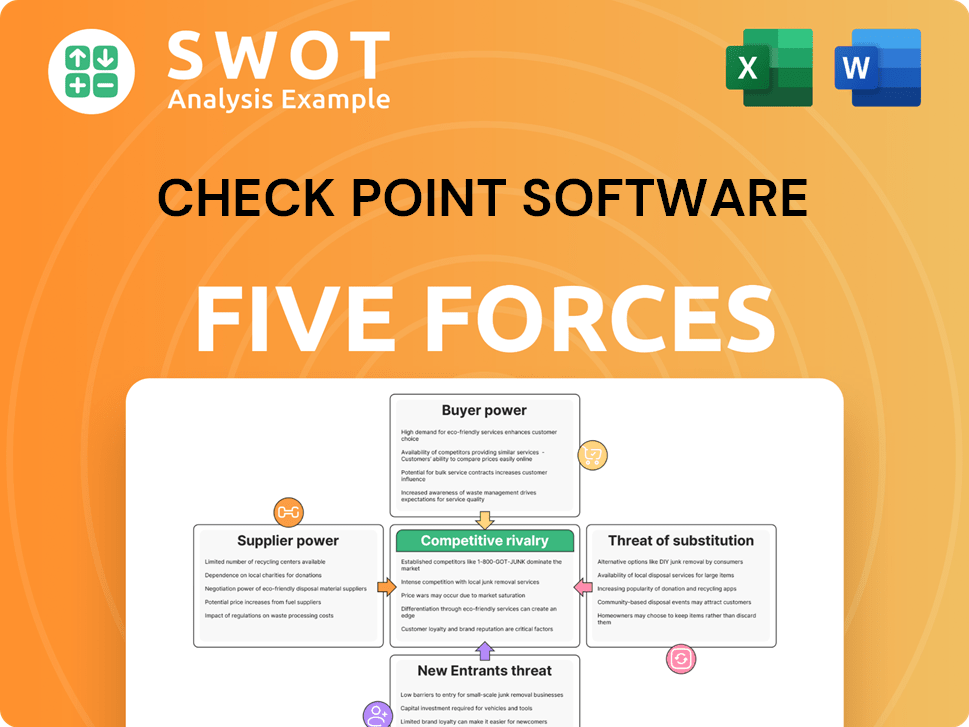
Check Point Software Porter's Five Forces Analysis
- Covers All 5 Competitive Forces in Detail
- Structured for Consultants, Students, and Founders
- 100% Editable in Microsoft Word & Excel
- Instant Digital Download – Use Immediately
- Compatible with Mac & PC – Fully Unlocked
Related Blogs
- What are Mission Vision & Core Values of Check Point Software Company?
- What is Competitive Landscape of Check Point Software Company?
- What is Growth Strategy and Future Prospects of Check Point Software Company?
- How Does Check Point Software Company Work?
- What is Sales and Marketing Strategy of Check Point Software Company?
- What is Brief History of Check Point Software Company?
- Who Owns Check Point Software Company?
Disclaimer
All information, articles, and product details provided on this website are for general informational and educational purposes only. We do not claim any ownership over, nor do we intend to infringe upon, any trademarks, copyrights, logos, brand names, or other intellectual property mentioned or depicted on this site. Such intellectual property remains the property of its respective owners, and any references here are made solely for identification or informational purposes, without implying any affiliation, endorsement, or partnership.
We make no representations or warranties, express or implied, regarding the accuracy, completeness, or suitability of any content or products presented. Nothing on this website should be construed as legal, tax, investment, financial, medical, or other professional advice. In addition, no part of this site—including articles or product references—constitutes a solicitation, recommendation, endorsement, advertisement, or offer to buy or sell any securities, franchises, or other financial instruments, particularly in jurisdictions where such activity would be unlawful.
All content is of a general nature and may not address the specific circumstances of any individual or entity. It is not a substitute for professional advice or services. Any actions you take based on the information provided here are strictly at your own risk. You accept full responsibility for any decisions or outcomes arising from your use of this website and agree to release us from any liability in connection with your use of, or reliance upon, the content or products found herein.