Check Point Software Bundle
Can Check Point Software Technologies Maintain Its Cybersecurity Edge?
The digital realm is a battlefield, and Check Point Software Technologies has been a key player in defending it since 1993. With the cybersecurity landscape constantly shifting, understanding the competitive pressures Check Point faces is crucial. This analysis delves into the company's evolution from firewall pioneer to a comprehensive security provider, exploring its strategic moves and market positioning.

From its early days, Check Point Software Technologies has navigated a complex Check Point Software SWOT Analysis to stay ahead. This examination of the Check Point competitive landscape will identify key Check Point competitors and analyze their impact. We'll also explore the company's product portfolio, market share, and financial performance, providing a comprehensive cybersecurity market analysis and insights into its future prospects, including a comparison with other firewall vendors and network security companies.
Where Does Check Point Software’ Stand in the Current Market?
Check Point Software Technologies maintains a substantial market position within the global cybersecurity industry, especially in network security. The company is recognized as a leader in enterprise firewall solutions, offering a range of products designed to protect various aspects of IT infrastructure. Its strategic focus includes expanding its offerings to address the evolving digital transformation needs of businesses worldwide, positioning itself as a comprehensive security provider.
Check Point's primary products include Quantum network security gateways, CloudGuard for cloud security, Harmony for endpoint and user security, and Infinity for a consolidated security architecture. These solutions cater to a wide array of customer segments, including large enterprises, service providers, and small to medium-sized businesses. This broad customer base and comprehensive product portfolio contribute to Check Point's strong competitive standing.
The company has strategically shifted its focus to offer a more unified and comprehensive security platform through its Check Point Infinity architecture. This architecture aims to simplify security management across various environments, including network, cloud, mobile, and endpoint. This move reflects Check Point's adaptation to the changing cybersecurity landscape and its commitment to providing integrated security solutions.
Check Point Software Technologies holds a significant market share in the network security sector. While specific figures for 2024-2025 are subject to ongoing market analysis, the company has consistently been a leading player, especially in enterprise firewall solutions. Its strong position allows it to compete effectively in the cybersecurity market.
Check Point offers a diverse product portfolio, including Quantum, CloudGuard, Harmony, and Infinity. This comprehensive suite of products supports its strategy to provide unified security solutions. The company's focus on integrated security platforms aims to simplify security management for its customers.
Check Point demonstrated strong financial performance in the first quarter of 2024, with revenues of $603 million, a 6% increase year-over-year. Subscription revenues grew by 13% to $252 million, indicating a successful shift towards recurring revenue models. This financial stability supports continued investment in research and development.
Check Point serves a broad customer base, including large enterprises, service providers, and SMBs. This diverse customer base, combined with a strong global presence, contributes to its market position. The company's ability to cater to various customer needs supports its competitive advantage.
Check Point's financial health, including its revenue growth and successful subscription model, allows for continued investment in research and development. This investment is crucial for maintaining a competitive edge in the rapidly evolving cybersecurity market. For a deeper understanding of the company's origins and development, you can explore Brief History of Check Point Software.
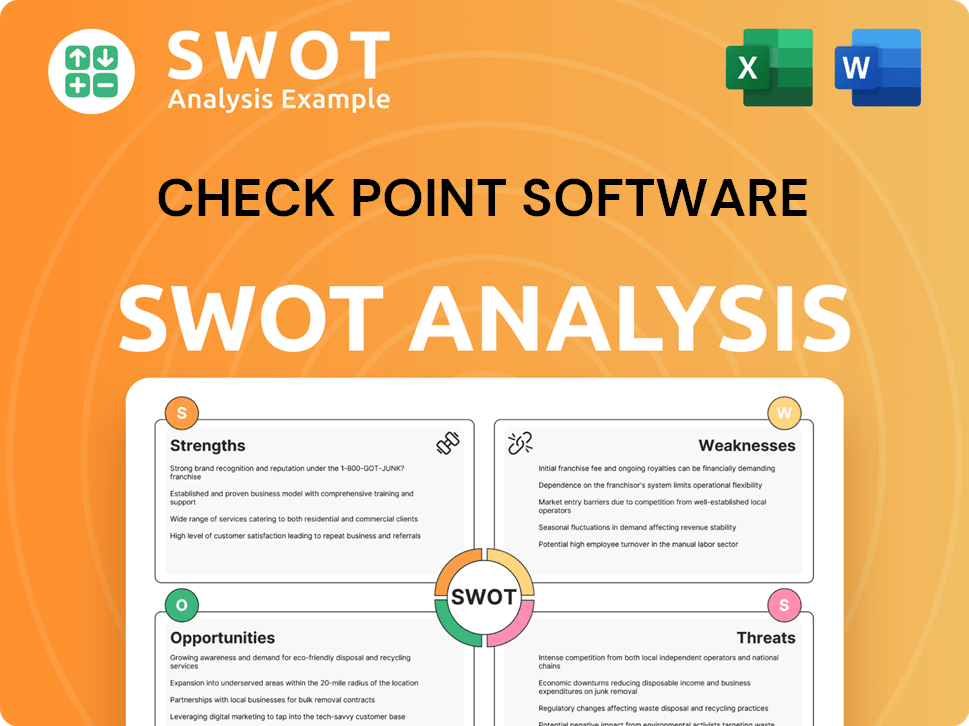
Check Point's key strengths include its strong market position in network security, a comprehensive product portfolio, and robust financial performance. These factors enable the company to compete effectively in the cybersecurity market. The company's strategic focus on unified security platforms further strengthens its competitive position.
- Strong presence in enterprise firewall solutions.
- Diversified product offerings, including cloud and endpoint security.
- Successful shift towards recurring revenue models.
- Broad customer base across various sectors.
Check Point Software SWOT Analysis
- Complete SWOT Breakdown
- Fully Customizable
- Editable in Excel & Word
- Professional Formatting
- Investor-Ready Format
Who Are the Main Competitors Challenging Check Point Software?
The competitive landscape for Check Point Software Technologies is dynamic, marked by intense competition across various cybersecurity segments. Understanding the key players and their strategies is crucial for assessing Check Point's market position and future prospects. The cybersecurity market is constantly evolving, with new threats and technologies emerging, requiring continuous adaptation and innovation from all participants.
Check Point's success depends on its ability to differentiate itself through product innovation, competitive pricing, and effective marketing. The company's financial performance and market share are directly impacted by its ability to compete effectively against these rivals. Analyzing the strengths and weaknesses of these competitors provides valuable insights into the challenges and opportunities Check Point faces.
Check Point Software Technologies faces a robust and diverse set of direct and indirect competitors across its various cybersecurity segments. In the critical network security and firewall market, key competitors include Palo Alto Networks, Fortinet, and Cisco. These companies compete on features, performance, and pricing, with each striving to capture a larger share of the market. A detailed Target Market of Check Point Software analysis reveals how these competitors target different customer segments.
Palo Alto Networks is a major competitor, known for its next-generation firewalls and cloud security offerings. They often compete with Check Point on advanced threat prevention and integrated security platforms. In 2024, Palo Alto Networks reported revenues of approximately $7.7 billion, highlighting its strong market presence.
Fortinet offers a broad portfolio of security solutions, including high-performance network security appliances. They often compete on price-performance and extensive product lines. Fortinet's revenue in 2024 reached around $5.3 billion, demonstrating its significant market share.
Cisco, with its vast networking infrastructure footprint, provides a wide array of security products, leveraging its existing customer base. Cisco's security revenue is substantial, though it is part of a larger networking business. In 2024, Cisco's security revenue was approximately $4.8 billion.
Zscaler specializes in cloud security and zero-trust solutions, challenging Check Point's cloud-focused offerings. Zscaler's revenue in 2024 was around $2.3 billion, reflecting its growth in the cloud security market.
CrowdStrike is a leader in endpoint security and cloud workload protection, often competing with Check Point's Harmony suite. CrowdStrike's revenue in 2024 was approximately $3.0 billion, showing its strong position in the endpoint and cloud security market.
Microsoft, with its comprehensive security services integrated into Azure and Microsoft 365, represents a significant competitor. Microsoft's security revenue is part of its broader cloud services, making it a formidable competitor. Microsoft's overall cloud revenue is substantial, exceeding $100 billion in 2024.
Beyond network security, in the cloud security domain, Check Point competes with cloud-native security providers such as Zscaler, CrowdStrike, and Microsoft Azure Security. These companies focus on different aspects of cloud security, creating a complex competitive environment. Furthermore, the competitive landscape also includes specialized vendors and emerging players. Mergers and acquisitions are constantly reshaping the competitive dynamics, with larger companies acquiring niche players to expand their portfolios. High-profile 'battles' often revolve around product innovation, the breadth of integrated platforms, and the ability to simplify security management for complex IT environments. The ability to offer comprehensive solutions that address evolving threats is a key factor in this competitive landscape.
Several factors drive competition in the cybersecurity market. These include technological innovation, pricing strategies, and the ability to provide comprehensive security solutions. The competitive landscape is constantly evolving, with new threats and technologies emerging.
- Product Innovation: Developing advanced security features and staying ahead of emerging threats.
- Pricing: Offering competitive pricing models to attract customers.
- Platform Integration: Providing integrated security platforms that simplify management.
- Customer Service: Delivering excellent customer support and service.
- Market Presence: Maintaining a strong brand reputation and global presence.
Check Point Software PESTLE Analysis
- Covers All 6 PESTLE Categories
- No Research Needed – Save Hours of Work
- Built by Experts, Trusted by Consultants
- Instant Download, Ready to Use
- 100% Editable, Fully Customizable
What Gives Check Point Software a Competitive Edge Over Its Rivals?
Understanding the Check Point competitive landscape is crucial for assessing its position in the cybersecurity market. Check Point Software Technologies has established itself as a key player, facing competition from various vendors. A deep dive into its competitive advantages reveals the strategies and strengths that define its market presence and future prospects. This analysis provides insights into the company's strengths, weaknesses, opportunities, and threats, offering a comprehensive view for investors and industry observers.
The company's success hinges on its ability to innovate and adapt to the ever-evolving cybersecurity landscape. Check Point's focus on a prevention-first approach, coupled with its integrated security architecture, aims to simplify security management for its customers. By examining its competitive advantages, we can better understand how Check Point Software Technologies aims to maintain its market position and drive future growth. This includes analyzing its product portfolio, customer base, and market positioning in relation to its competitors.
For those interested in the financial aspects, a review of Owners & Shareholders of Check Point Software can provide additional context on the company's financial performance and ownership structure.
Check Point's competitive advantage stems from its foundational expertise in network security, particularly its pioneering stateful inspection firewall technology. This technology forms the basis of its Quantum network security gateways. This long-standing experience allows it to offer robust threat prevention capabilities, setting it apart in the competitive cybersecurity market.
A key differentiator for Check Point is its prevention-first approach, which prioritizes blocking threats before they can cause damage. This strategy contrasts with the detection and response methods often employed by competitors. By focusing on proactive threat prevention, Check Point aims to reduce the impact of cyberattacks on its customers.
The Check Point Infinity architecture provides a consolidated security platform across network, cloud, mobile, and endpoint environments. This integrated approach simplifies security management and reduces complexity for customers. It offers a unified security posture, leveraging shared intelligence and centralized management for enhanced security effectiveness.
Check Point benefits from strong brand equity and a loyal customer base, built on years of delivering reliable security solutions. This established trust is a significant advantage in the cybersecurity market. The company's commitment to customer satisfaction and its proven track record contribute to its competitive edge.
Check Point Software Technologies maintains a strong competitive position through several key advantages. These include its deep expertise in network security, a prevention-first approach, and the Check Point Infinity architecture. These strengths enable the company to effectively compete in the dynamic cybersecurity market.
- Proprietary Technologies: Check Point's stateful inspection firewall technology and Quantum network security gateways provide robust threat prevention.
- Integrated Platform: The Check Point Infinity architecture simplifies security management across various environments.
- Strong Brand: A loyal customer base and established brand equity support Check Point's market presence.
- R&D and Threat Intelligence: Continuous innovation and threat intelligence capabilities keep Check Point ahead of evolving cyber threats.
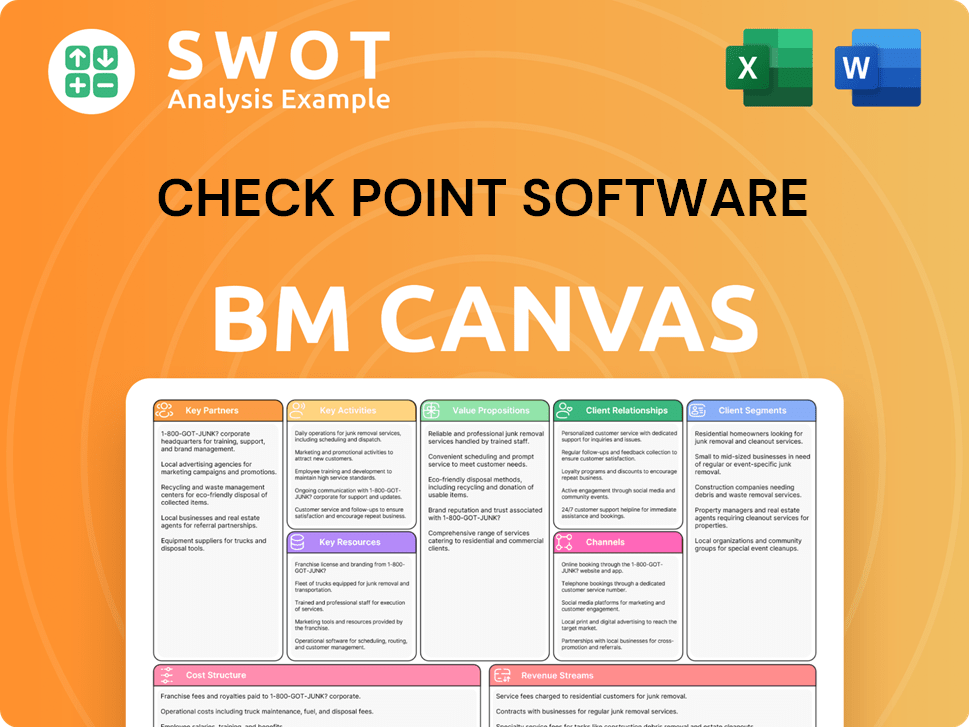
Check Point Software Business Model Canvas
- Complete 9-Block Business Model Canvas
- Effortlessly Communicate Your Business Strategy
- Investor-Ready BMC Format
- 100% Editable and Customizable
- Clear and Structured Layout
What Industry Trends Are Reshaping Check Point Software’s Competitive Landscape?
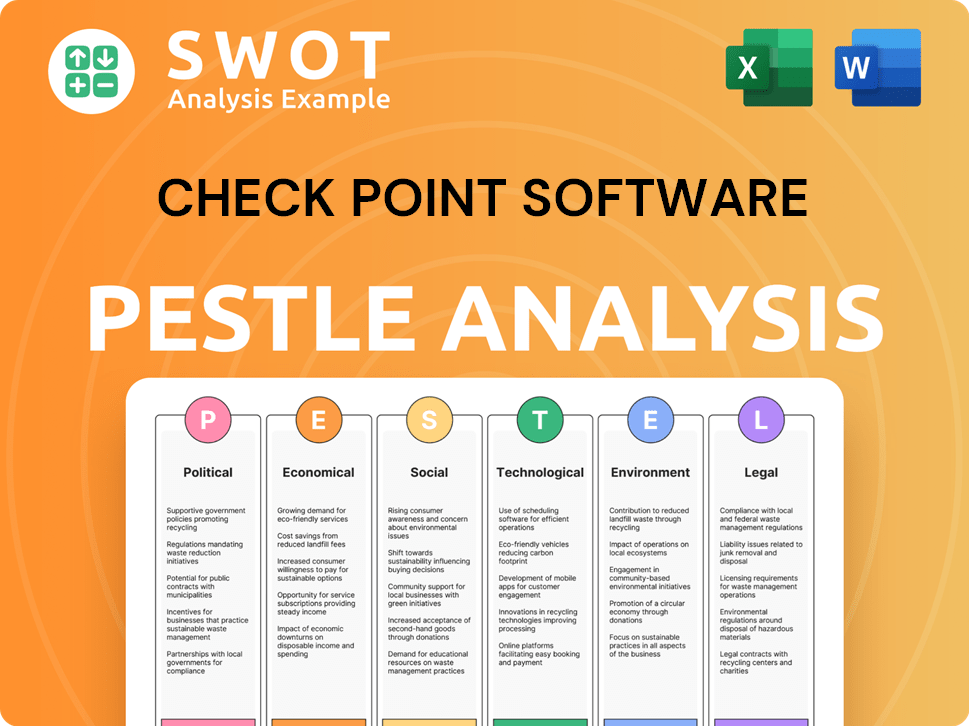
The cybersecurity industry is experiencing dynamic shifts, significantly impacting companies like Check Point Software Technologies. Key trends such as cloud computing, the rise of sophisticated cyber threats, and the adoption of AI are reshaping the market. These factors present both challenges and opportunities for Check Point as it navigates the competitive landscape.
Check Point's future depends on its ability to adapt to these changes and maintain its competitive edge. This involves continuous innovation, strategic partnerships, and a focus on customer needs. Understanding the evolving cybersecurity market is crucial for Check Point's sustained success.
The cybersecurity market is driven by the increasing adoption of cloud computing, with cloud security spending projected to reach $75.3 billion in 2024. Cyber threats are becoming more sophisticated, necessitating advanced threat prevention. AI and machine learning are being integrated for threat detection and automation, as evidenced by the growing use of AI in security solutions.
Check Point faces intense competition from established players and agile startups. The cybersecurity talent shortage impacts innovation and service delivery. The demand for simplified, integrated, and cost-effective solutions is also increasing. Companies like Palo Alto Networks and Cisco, are strong competitors in the firewall vendors market.
Significant growth opportunities exist in emerging markets and expanding managed security services. Strategic partnerships can extend reach and capabilities. The platform-centric approach, emphasizing consolidation and automation, can address customer complexity. Check Point's focus on its Infinity architecture is crucial.
The competitive landscape is evolving towards a platform-centric approach. Continuous innovation and strategic acquisitions are key. Check Point's ability to adapt and innovate will determine its market share. Understanding the Growth Strategy of Check Point Software is essential for navigating the competitive environment.
Check Point's future success depends on several key strategies, including technological innovation and market expansion. The company must continue to invest in R&D to stay ahead of evolving threats and customer demands. Strategic partnerships and acquisitions will be crucial for expanding its market reach and capabilities.
- Focus on Cloud Security: Expand and enhance the CloudGuard offerings to capitalize on the growing cloud market.
- Enhance Threat Intelligence: Continuously improve threat detection and prevention capabilities using AI and machine learning.
- Expand Managed Security Services: Offer comprehensive managed security services to meet the needs of organizations with limited in-house expertise.
- Strategic Partnerships: Forge partnerships to extend market reach and integrate complementary technologies.
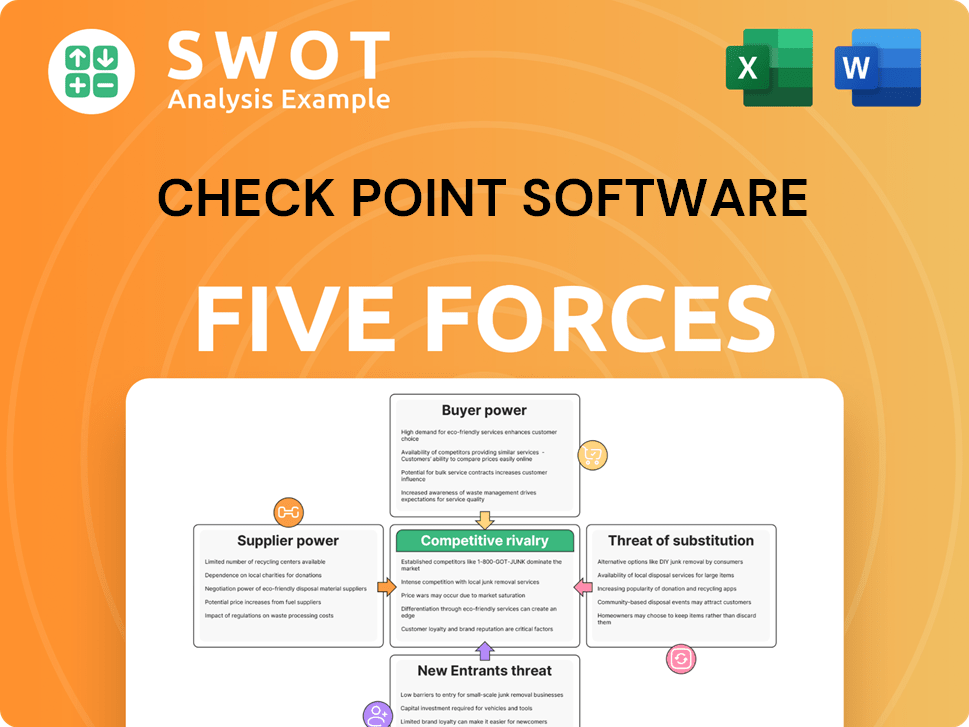
Check Point Software Porter's Five Forces Analysis
- Covers All 5 Competitive Forces in Detail
- Structured for Consultants, Students, and Founders
- 100% Editable in Microsoft Word & Excel
- Instant Digital Download – Use Immediately
- Compatible with Mac & PC – Fully Unlocked
Related Blogs
- What are Mission Vision & Core Values of Check Point Software Company?
- What is Growth Strategy and Future Prospects of Check Point Software Company?
- How Does Check Point Software Company Work?
- What is Sales and Marketing Strategy of Check Point Software Company?
- What is Brief History of Check Point Software Company?
- Who Owns Check Point Software Company?
- What is Customer Demographics and Target Market of Check Point Software Company?
Disclaimer
All information, articles, and product details provided on this website are for general informational and educational purposes only. We do not claim any ownership over, nor do we intend to infringe upon, any trademarks, copyrights, logos, brand names, or other intellectual property mentioned or depicted on this site. Such intellectual property remains the property of its respective owners, and any references here are made solely for identification or informational purposes, without implying any affiliation, endorsement, or partnership.
We make no representations or warranties, express or implied, regarding the accuracy, completeness, or suitability of any content or products presented. Nothing on this website should be construed as legal, tax, investment, financial, medical, or other professional advice. In addition, no part of this site—including articles or product references—constitutes a solicitation, recommendation, endorsement, advertisement, or offer to buy or sell any securities, franchises, or other financial instruments, particularly in jurisdictions where such activity would be unlawful.
All content is of a general nature and may not address the specific circumstances of any individual or entity. It is not a substitute for professional advice or services. Any actions you take based on the information provided here are strictly at your own risk. You accept full responsibility for any decisions or outcomes arising from your use of this website and agree to release us from any liability in connection with your use of, or reliance upon, the content or products found herein.