Check Point Software Bundle
Can Check Point Software Thrive in the Face of Escalating Cyber Threats?
In today's digital battlefield, the growth strategy of a cybersecurity company like Check Point Software is not just important; it's essential. With cyber-attacks surging and threats becoming increasingly sophisticated, understanding Check Point's approach to securing the future is critical. This analysis explores the company's strategic moves, including recent acquisitions, and its commitment to innovation in a rapidly evolving landscape.

Check Point Software, a leading cybersecurity company, is navigating a complex market, and this exploration dives deep into its Check Point Software SWOT Analysis. We'll examine its growth strategy, from its early firewall solutions to its current AI-powered security solutions, and assess its future outlook. This includes a detailed market analysis of the cybersecurity industry, its financial performance, and the potential for long-term growth, considering emerging threats and strategic partnerships.
How Is Check Point Software Expanding Its Reach?
Check Point Software Technologies is actively pursuing expansion through several key initiatives. The company focuses on penetrating new markets, developing its product pipeline, and making strategic acquisitions. Its strategy involves refining go-to-market approaches and emphasizing a hybrid mesh network architecture. These efforts aim to solidify its position as a leading cybersecurity company.
A significant area of expansion is in cloud security and SASE. Acquisitions like Perimeter81 and CyberInt in 2023 have played a crucial role in bolstering these capabilities. These acquisitions aim to diversify revenue streams and address the growing demand for comprehensive cloud and edge security solutions. This is particularly important as organizations shift more workloads to the cloud, expanding their attack surface.
The company is also strengthening its core product lines, such as Check Point Quantum for enterprise-grade network security, and placing a strong emphasis on SASE. Check Point's Infinity consolidated platform is a key driver for customer adoption and sustainable growth. Customers increasingly seek to consolidate their cybersecurity vendors. This platform unifies the management of on-premises, cloud, and workspace environments, offering flexibility, simplicity, and scale.
Check Point is focused on expanding its reach into new markets. This involves tailoring its security solutions to meet the specific needs of different regions and industries. Simultaneously, the company is investing heavily in the development of new products and features to stay ahead of emerging cybersecurity threats. This includes enhancing existing offerings and creating innovative solutions.
Strategic acquisitions are a key part of Check Point's growth strategy. The acquisitions of Perimeter81 and CyberInt in 2023 are prime examples. These acquisitions enable Check Point to quickly add new technologies and expertise. These moves help to broaden its portfolio of security solutions and enhance its competitive advantage in the cybersecurity market.
Check Point is significantly expanding its cloud security and SASE capabilities. This expansion is driven by the increasing adoption of cloud services by businesses. The company is investing in technologies that provide comprehensive security for cloud environments. This includes solutions for protecting data, applications, and infrastructure in the cloud.
The company continues to strengthen its core product lines, such as Check Point Quantum for enterprise-grade network security. This involves ongoing improvements to existing products and the development of new features. Check Point is focused on delivering high-performance security solutions. These solutions protect against a wide range of cyber threats.
Check Point is also expanding its global team, with career opportunities across engineering, cyber threat research, and sales. This indicates a commitment to scaling its workforce to support growth. The company's focus on innovation and customer needs is evident in its product development and strategic partnerships. For instance, in 2024, the cybersecurity market is projected to reach a value of over $200 billion, reflecting the importance of companies like Check Point in this space. To understand the competitive landscape, consider the Competitors Landscape of Check Point Software.
Check Point's expansion efforts focus on several key areas to drive growth and maintain its competitive edge. These areas include cloud security, SASE, and the continued enhancement of core product lines. The company is also investing in market penetration and strategic acquisitions to broaden its reach and capabilities.
- Cloud Security: Expanding cloud security solutions to protect data and applications.
- SASE: Strengthening SASE capabilities to provide secure access to applications and data.
- Core Product Lines: Enhancing core products like Check Point Quantum.
- Market Penetration: Targeting new markets and customer segments.
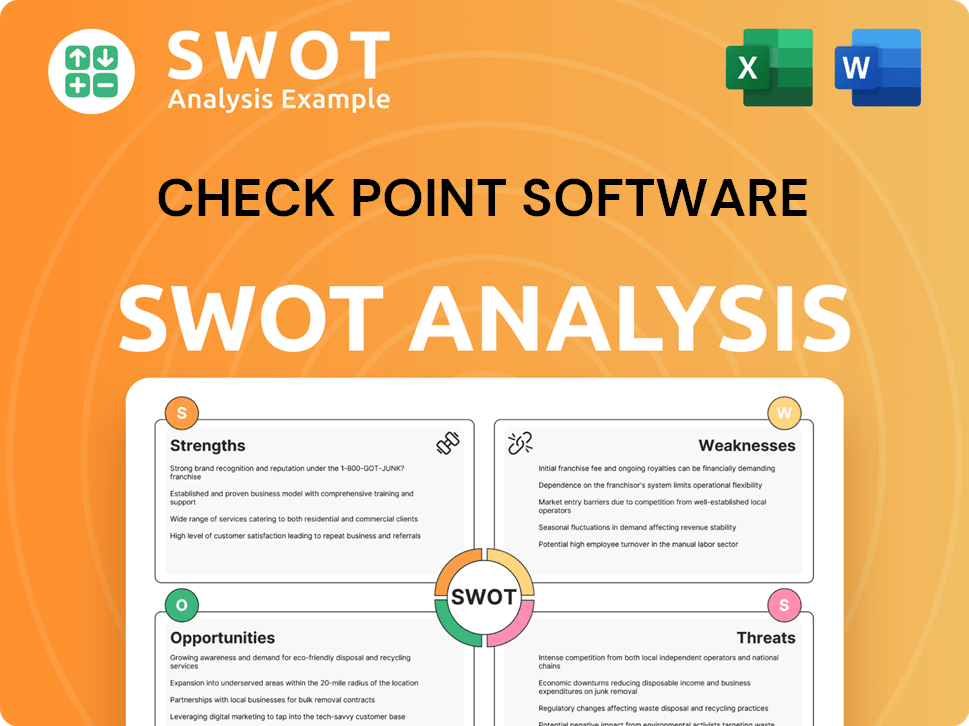
Check Point Software SWOT Analysis
- Complete SWOT Breakdown
- Fully Customizable
- Editable in Excel & Word
- Professional Formatting
- Investor-Ready Format
How Does Check Point Software Invest in Innovation?
Check Point Software Technologies focuses on innovation and technology to fuel its growth. The company prioritizes significant investments in research and development, particularly in AI-powered solutions, to stay ahead in the cybersecurity market. This strategy allows it to offer cutting-edge security solutions, driving its long-term growth prospects.
The company's approach to digital transformation and automation is centered around its AI-powered Infinity Platform, which aims to enhance cybersecurity efficiency and accuracy with industry-leading catch rates for proactive threat anticipation and faster response times. Check Point's commitment to AI is further highlighted by its inaugural AI Security Report, launched at the RSA Conference 2025, which details how cybercriminals use AI for deceptive tactics and outlines strategies for defense.
This commitment to innovation is reflected in its intellectual property portfolio and industry recognition. The company consistently receives accolades for its advanced technologies and strategic vision, reinforcing its position as a leading cybersecurity company. This focus on innovation is crucial for navigating the evolving cybersecurity landscape and maintaining a competitive edge.
Check Point Software's R&D expenses for 2024 reached $0.395 billion. For the twelve months ending March 31, 2025, these expenses increased to $0.398 billion.
The Infinity Platform integrates cloud-delivered technologies. This includes Check Point Harmony for workspace security, Check Point CloudGuard for cloud security, and Check Point Quantum for network security.
Check Point predicts that by 2025, AI will be a major driver of both attacks and protections. Security teams will rely heavily on AI-powered tools.
In Q2 2024, nearly 29% of Check Point's artificial intelligence patents were filed. Approximately 11% of these patents were granted.
Recent patents include innovations in phishing detection using HTML (granted November 2024) and techniques for securing services using inter-service visibility (granted April 2025).
Check Point was named one of America's Best Cybersecurity Companies in 2025 by Newsweek and Statista. It was also recognized as one of the World's Best Companies by TIME and Statista in 2024.
Check Point's growth strategy is heavily reliant on technological innovation, particularly in AI and cloud security. Its focus on R&D and strategic partnerships supports its competitive position in the cybersecurity market. The company's ability to adapt to emerging cybersecurity threats will be critical for its future outlook.
- AI-Powered Solutions: Development and deployment of AI-driven tools for threat detection and response.
- Cloud Security: Enhancing cloud security solutions to meet the growing demand for secure cloud environments.
- R&D Investments: Continuous investment in research and development to create cutting-edge cybersecurity technologies.
- Strategic Partnerships: Collaborations with other companies to expand market reach and enhance product offerings.
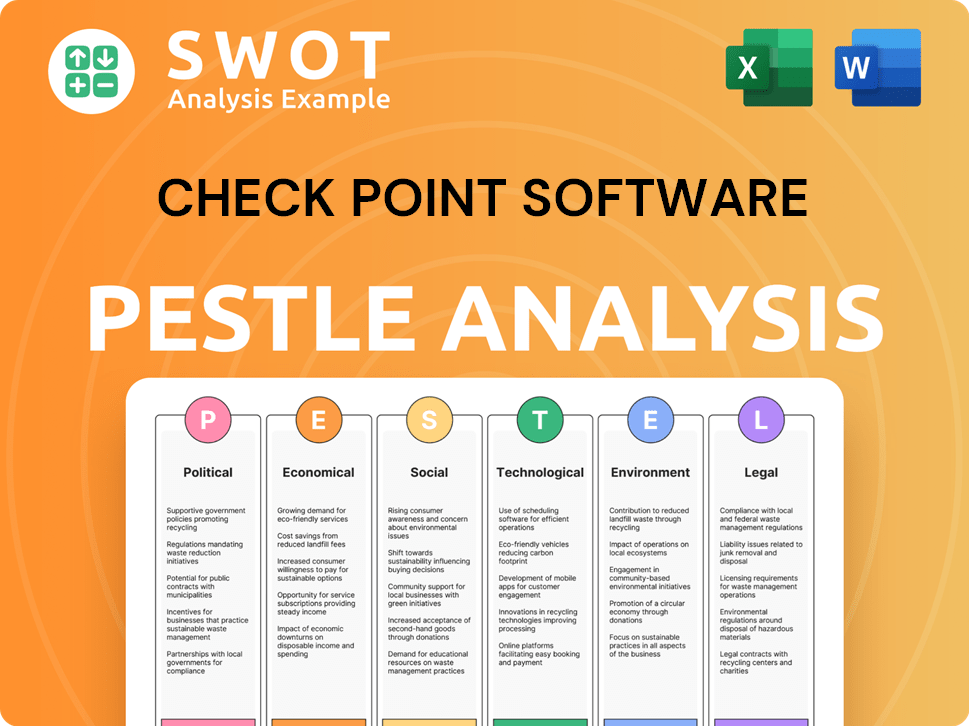
Check Point Software PESTLE Analysis
- Covers All 6 PESTLE Categories
- No Research Needed – Save Hours of Work
- Built by Experts, Trusted by Consultants
- Instant Download, Ready to Use
- 100% Editable, Fully Customizable
What Is Check Point Software’s Growth Forecast?
The financial outlook for Check Point Software Technologies, a prominent cybersecurity company, presents a picture of stability and consistent profitability. While the firm demonstrates solid financial health, its growth trajectory lags behind some of its more aggressive competitors in the cybersecurity market. This difference is reflected in its valuation compared to industry peers.
For the fiscal year 2024, the company reported total revenues of $2.565 billion, reflecting a 6% year-over-year increase. The growth in Security Subscriptions Revenues was particularly notable, increasing by 13% to $1.104 billion in 2024. This indicates a robust demand for its security solutions and services.
Check Point Software's financial performance showcases a strong commitment to shareholder value and strategic investment. The company's focus on returning value to shareholders through share repurchases and its healthy cash position are key indicators of its financial strength. To understand more about its potential target market, you can explore the Target Market of Check Point Software.
Check Point Software's revenue grew by 6% in 2024, reaching $2.565 billion. This growth, while positive, is moderate compared to some competitors in the cybersecurity market. The company's ability to accelerate revenue growth will be crucial for its future outlook.
The gross profit margin for Check Point Software has been consistently high, averaging 88.5% from December 2020 to 2024. The non-GAAP operating margin for 2024 was 44%, demonstrating efficient operations and strong profitability.
Analysts project Check Point's revenue for FY 2025 to be around $2.718 billion. Earnings per share (EPS) are expected to be between $9.90 and $10.20, reflecting continued profitability and financial stability. The non-GAAP EPS increased by 9% to $9.16 for the full year 2024.
Check Point Software maintains a strong cash position, holding more cash than debt. In 2024, the company repurchased approximately 7.7 million shares for $1.3 billion. The cash flow from operations was $1.059 billion as of the end of 2024.
Check Point Software trades at a discount compared to its peers, with an estimated FY 2025 EV/Sales multiple of 7.5x versus a peer group average of 10.3x. This valuation gap reflects the company's growth rate compared to more aggressive competitors in the cybersecurity market trends.
- The company faces challenges in accelerating top-line growth compared to some industry peers.
- The company's growth strategy must focus on innovation and market expansion.
- Market analysis reveals a competitive landscape with rapid changes.
- Check Point Software needs to invest in research and development to stay competitive.
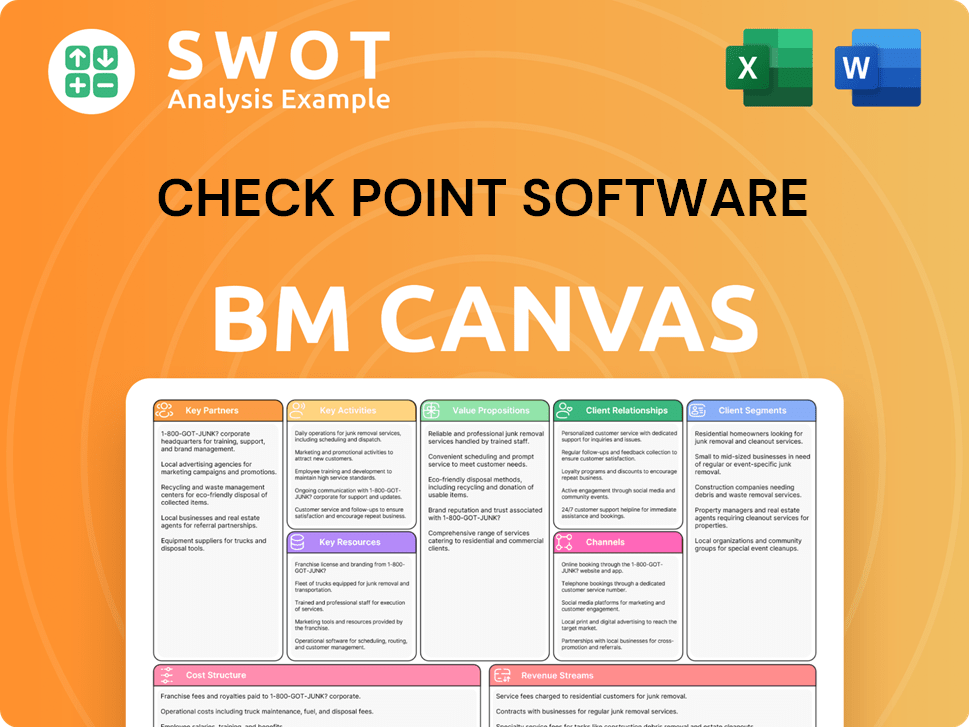
Check Point Software Business Model Canvas
- Complete 9-Block Business Model Canvas
- Effortlessly Communicate Your Business Strategy
- Investor-Ready BMC Format
- 100% Editable and Customizable
- Clear and Structured Layout
What Risks Could Slow Check Point Software’s Growth?
The path of Check Point Software towards sustained growth is fraught with potential risks and obstacles. The cybersecurity landscape is dynamic and competitive, requiring constant adaptation and innovation to stay ahead. Understanding these challenges is crucial for evaluating the company's growth strategy and its ability to maintain a strong position in the market.
Competition from major players and the constant evolution of cyber threats pose significant hurdles. These factors can impact Check Point Software's financial performance and its ability to capture market share. Addressing these challenges effectively is critical for the company's long-term success and for investors assessing its future outlook.
Technological disruptions, such as the increasing use of AI in cyberattacks and the emergence of quantum computing, represent substantial risks. The company's ability to adapt to these changes and invest in cutting-edge security solutions will be critical for its future. Moreover, supply chain vulnerabilities and geopolitical tensions further complicate the risk landscape, requiring proactive and robust security measures.
The cybersecurity market is highly competitive, with rivals like Palo Alto Networks, Fortinet, and Cisco Systems vying for market share. While customer loyalty can benefit Check Point Software, its growth rates have lagged behind some competitors, raising questions about its long-term market share and affecting its financial performance.
Rapid technological advancements and evolving threats, including AI-driven attacks, pose significant risks. The misuse of AI and the looming threat of quantum computing necessitate continuous innovation in security solutions. Check Point Software must stay ahead of these trends to maintain its competitive edge.
Threat actors increasingly target third-party code and open-source libraries, creating significant supply chain vulnerabilities. The Linux XZ vulnerability in March 2024 is a prime example of this risk. Addressing these vulnerabilities requires robust security measures and proactive threat management.
Geopolitical tensions and regulatory changes can destabilize systems and erode trust. Nation-state cyber campaigns and evolving data privacy regulations add to the risk landscape. Check Point Software must navigate these complexities to maintain its market position and ensure compliance.
Investments in R&D and the Infinity platform may pressure profitability in the near term. Operating margins have compressed, from 58% in 2014 to an estimated 43% in 2024. Managing these investments effectively is critical for maintaining profitability and driving long-term growth prospects.
Proactive patch management is crucial, as 96% of exploits in 2024 leveraged vulnerabilities disclosed prior to the year. Strengthening authentication and access controls, and adopting Zero Trust architectures, are essential for mitigating threats. Check Point Software's focus on these areas will determine its future market share.
To address these risks, Check Point Software focuses on continuous investment in R&D and its Infinity platform, which provides comprehensive security architecture. The company emphasizes strengthening authentication, access controls, and adopting Zero Trust architectures alongside AI-enhanced threat detection systems. The company's approach is designed to address emerging cybersecurity threats.
The cybersecurity market is expected to continue growing, driven by increasing cyber threats and the need for robust security solutions. However, Check Point Software must navigate intense competition and technological disruptions to capitalize on this growth. For a deeper dive, you can read more about the company's growth strategy analysis.
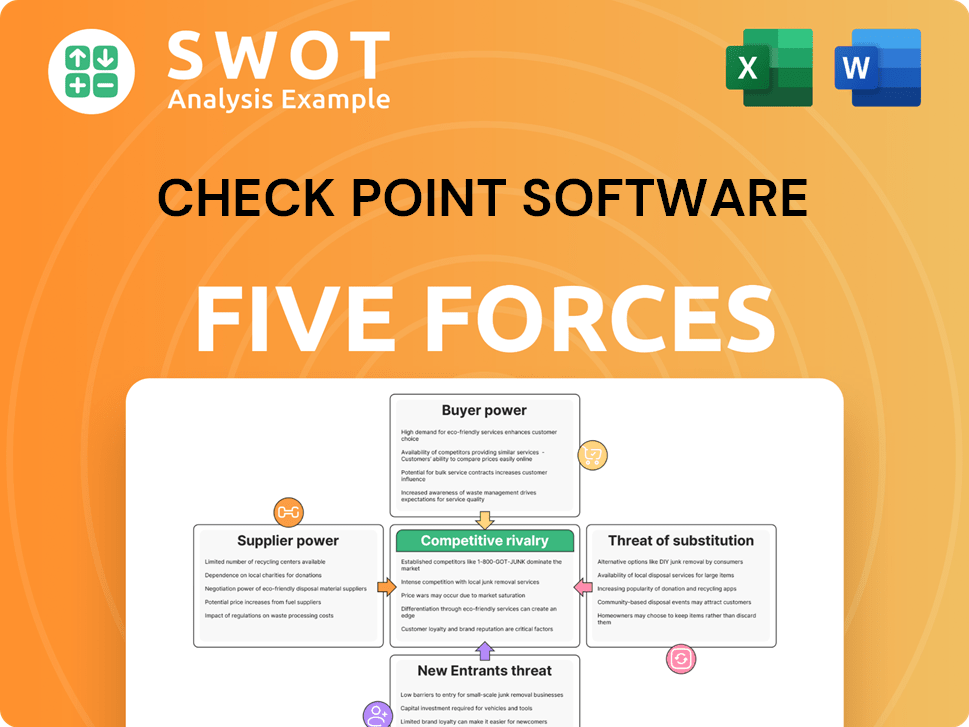
Check Point Software Porter's Five Forces Analysis
- Covers All 5 Competitive Forces in Detail
- Structured for Consultants, Students, and Founders
- 100% Editable in Microsoft Word & Excel
- Instant Digital Download – Use Immediately
- Compatible with Mac & PC – Fully Unlocked
Related Blogs
- What are Mission Vision & Core Values of Check Point Software Company?
- What is Competitive Landscape of Check Point Software Company?
- How Does Check Point Software Company Work?
- What is Sales and Marketing Strategy of Check Point Software Company?
- What is Brief History of Check Point Software Company?
- Who Owns Check Point Software Company?
- What is Customer Demographics and Target Market of Check Point Software Company?
Disclaimer
All information, articles, and product details provided on this website are for general informational and educational purposes only. We do not claim any ownership over, nor do we intend to infringe upon, any trademarks, copyrights, logos, brand names, or other intellectual property mentioned or depicted on this site. Such intellectual property remains the property of its respective owners, and any references here are made solely for identification or informational purposes, without implying any affiliation, endorsement, or partnership.
We make no representations or warranties, express or implied, regarding the accuracy, completeness, or suitability of any content or products presented. Nothing on this website should be construed as legal, tax, investment, financial, medical, or other professional advice. In addition, no part of this site—including articles or product references—constitutes a solicitation, recommendation, endorsement, advertisement, or offer to buy or sell any securities, franchises, or other financial instruments, particularly in jurisdictions where such activity would be unlawful.
All content is of a general nature and may not address the specific circumstances of any individual or entity. It is not a substitute for professional advice or services. Any actions you take based on the information provided here are strictly at your own risk. You accept full responsibility for any decisions or outcomes arising from your use of this website and agree to release us from any liability in connection with your use of, or reliance upon, the content or products found herein.